"VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in your VPC. Flow log data can be published to Amazon CloudWatch Logs and Amazon S3." (source: here)
The following tool enables:
- Detection of VPC's without flow log audit enabled
- Remediation by enabling auditing of all new VPC's into a single new s3 bucket with lifecycle rule of 365 days.
- Valid access keys at
~/.aws/credentialswith a default profile configured or matching AWS Environment Variables PythonandPipenvinstalled on the host running the tool
git clone https://github.com/bridgecrewio/HowCrew.git
cd HowCrew/
pipenv install
pipenv run python setup-vpc-flow-logs/setup_vpc_flow_logs.py --help$ pipenv run python setup-vpc-flow-logs/setup_vpc_flow_logs.py --help
usage: setup_vpc_flow_logs.py [-h]
{describe_vpcs_flow_log,enable_flow_logs} ...
positional arguments:
{describe_vpcs_flow_log,enable_flow_logs}
describe_vpcs_flow_log
List all vpc instances and their flow log status along
side related region and tags.
enable_flow_logs Enables flow logs to VPCs that do not have flow log
enabled
optional arguments:
-h, --help show this help message and exit
pipenv run python setup-vpc-flow-logs/setup_vpc_flow_logs.py describe_vpcs_flow_log| VpcId | Flow log Enabled | Region | Tags |
|----------+------------------+-----------+-----------------------------------|
| vpc-09aa | TRUE | us-west-2 | {cf-stack=app-stack},{stage=prod} |
| vpc-09bb | TRUE | us-west-2 | {cf-stack=db-stack},{stage=dev} |
| vpc-09cc | FALSE | us-east-1 | {cf-stack=es-stack} |
usage: setup_vpc_flow_logs.py enable_flow_logs [-h] [-b BUCKET]
optional arguments:
-h, --help show this help message and exit
-b BUCKET, --bucket BUCKET
determines the name of the new flow log bucket. All
flow logs will be listed in the path pattern: bucket_A
RN/optional_folder/AWSLogs/aws_account_id/vpcflowlogs/
region/year/month/day/aws_account_id_vpcflowlogs_regio
n_flow_log_id_timestamp_hash.log.gz Bucket is created
with lifecycle rule to expire logs older then 365 days.
Bucket will have versioning turned on.
Bucket will have Block all public access turned on.
NOTICE: flow logs will be created for all VPCs that do not have one
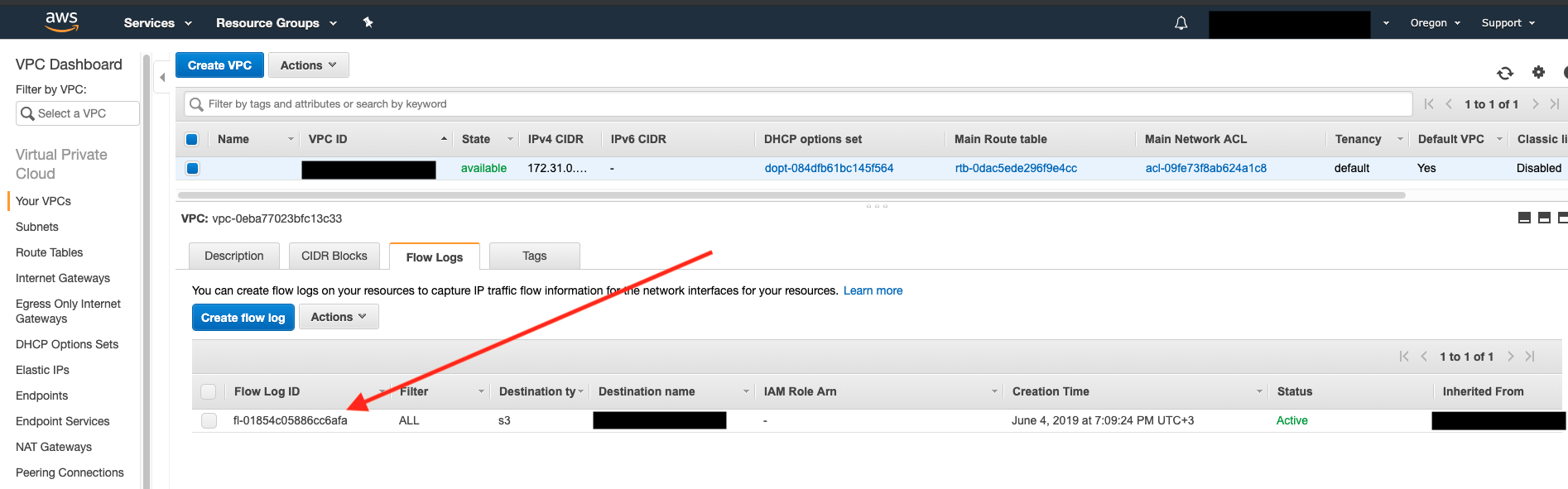
Flow logs configured for all VPCs that did not have one enabled:
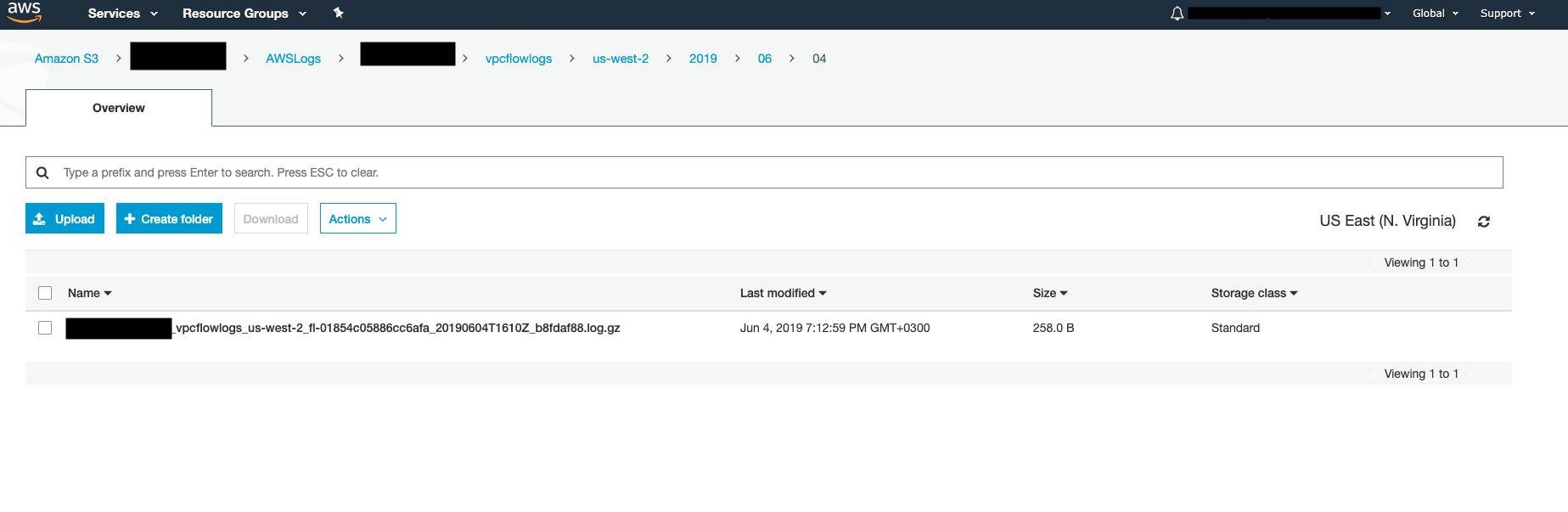
A new s3 bucket with vpc flow logs:
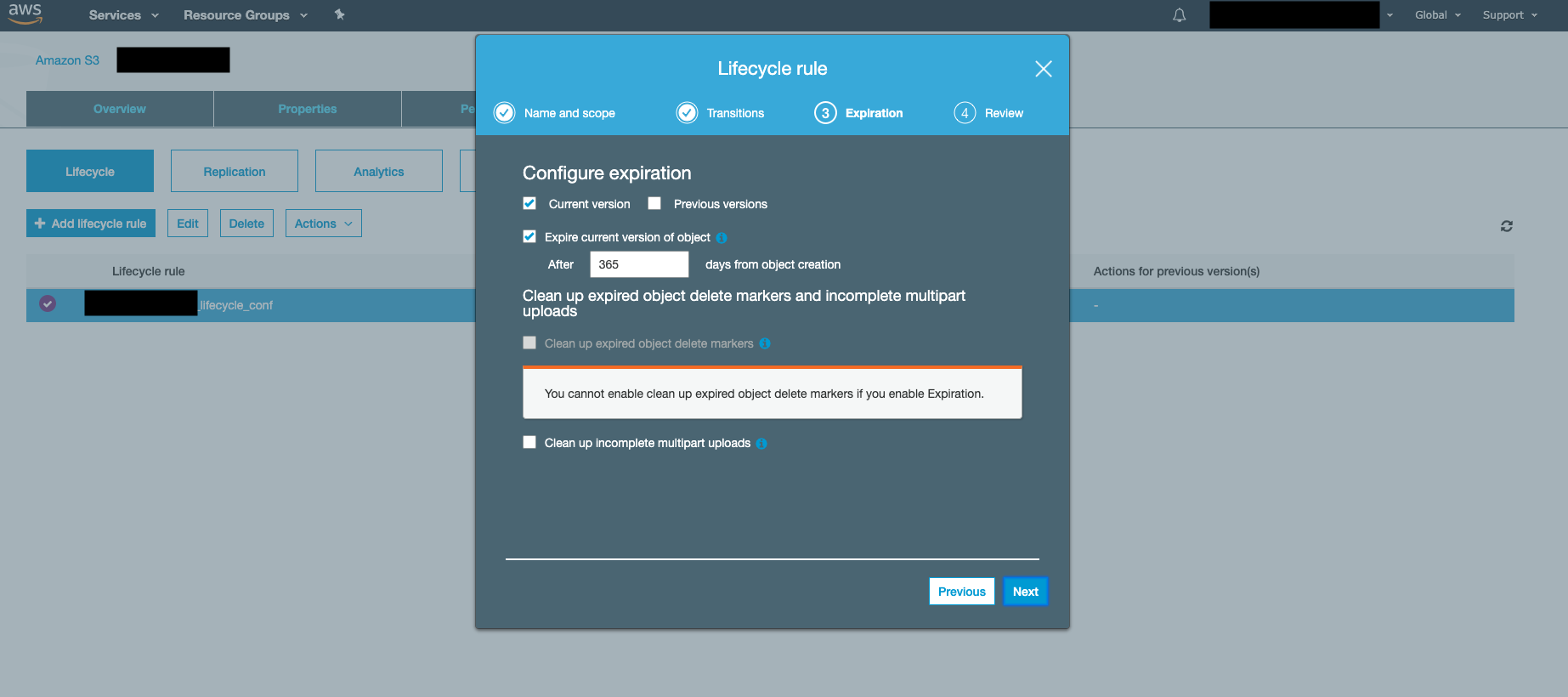
Lifecycle expiration policy on the s3 bucket:
For forensic purposes, you can configure to view VPC flow data via AWS Athena (or any other forensic tool). For further details see the official guide.