-
-
Notifications
You must be signed in to change notification settings - Fork 387
FS_Process_Modules
The directory modules exists as a sub-directory in each process directory.
The modules directory contains one sub-directory for each loaded module (.DLLs and EXEs). It also contains the modules.txt and unloaded_modules.txt info files with shorthand information about each module.
For kernel "processes" such as the System process in Windows (PID 4) the directory will contain loaded drivers (.SYS-files and .DLLs)
Each module directory contains a number of informational files and directories related to the loaded module. The files and directories and their contents are listed below:
| File | Description |
|---|---|
| base.txt | Base virtual address of the module |
| directories.txt | Information about the 16 data directories in the PE/MZ header |
| entry.txt | Entry point virtual address of the module |
| export.txt | Functions exported by the module |
| import.txt | Functions imported by the module and their corresponding modules |
| pefile.dll | Best-effort reconstructed module, .exe/.dll/.sys, file from memory fragments |
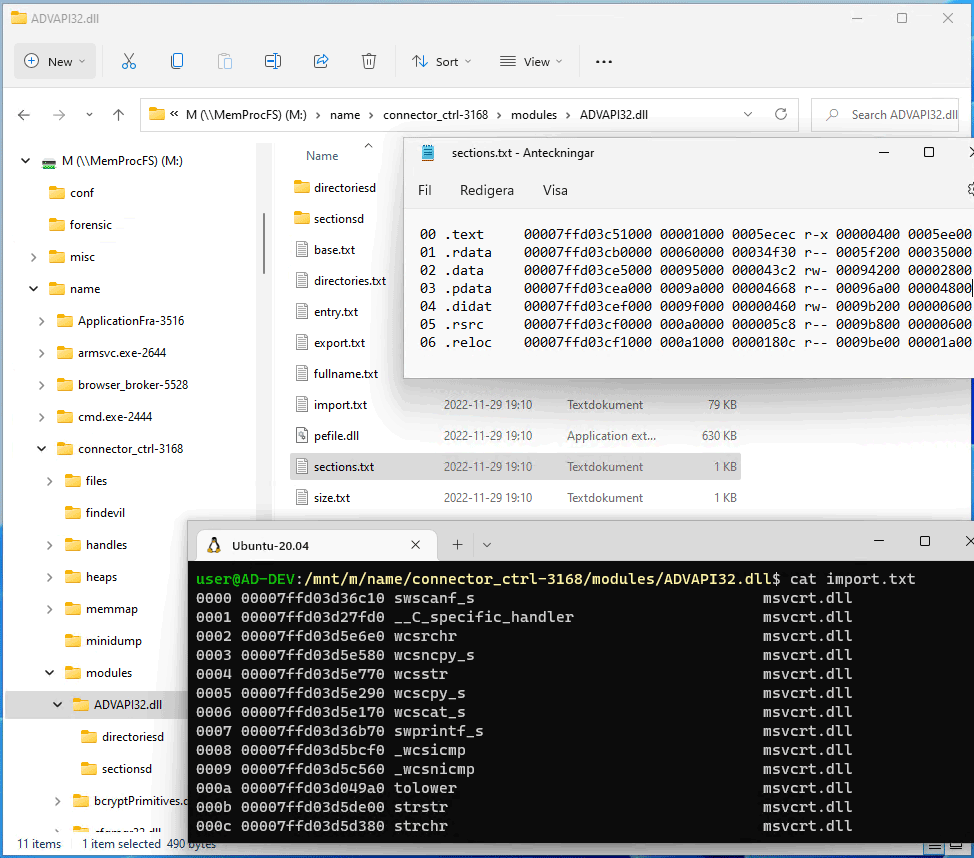
| sections.txt | Sections of the module |
| size.txt | Size of the module |
| directoriesd | Directory containing a file for each of the 16 data directories |
| sectionsd | Directory containing a file for each section |
Files in the individual module directories are read-only. pefile.dll and files in the directoriesd and sectionsd sub-directories are writable if a write-capable memory acquisition device is used.
The file export.txt contains information about exported functions. The meaning of the columns are as follows:
# ordinal fn_offset function_address function_name
======================================================
0000 1000 37410 00007ffd77347410 ---
0001 1001 2c880 00007ffd7733c880 I_ScGetCurrentGroupStateW
0002 1002 91868 00007ffd773a1868 A_SHAFinal
0003 1003 91883 00007ffd773a1883 A_SHAInit
0004 1004 9189f 00007ffd773a189f A_SHAUpdate
0005 1005 41890 00007ffd77351890 AbortSystemShutdownA
The file sections.txt contains information about the module PE sections. The meaning of the columns are as follows:
# name memory_address base_offset size page file_offset size
=====================================================================
00 .text 00007ff7959a1000 00001000 0002e338 r-x 00000400 0002e400
...
05 .rsrc 00007ff7959fb000 0005b000 000084f8 r-- 0003b600 00008600
06 .reloc 00007ff795a04000 00064000 00000308 r-- 00043c00 00000400
The example below shows the files in the modules/Actioncenter.dll sub-directory of the explorer.exe process. All files are related to the Actioncenter.dll module which is loaded into the explorer.exe process.
Shown in Notepad++ are the sections of the .DLL. While Ubuntu shows the entry, size, exported functions and the three first imported functions.
The modules sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file m_proc_ldrmodules.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖