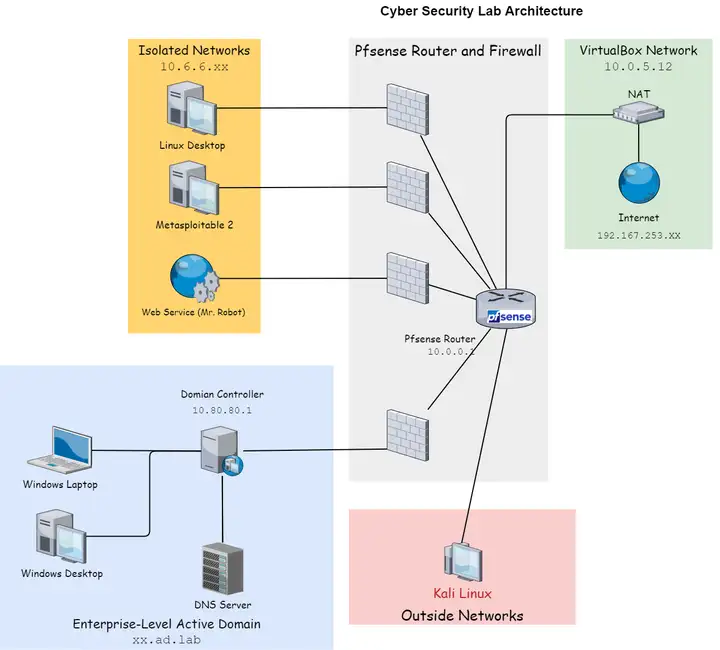
We use this repo to test out if an AI that was trained in a simulated cyber range (e.g.Network Attack Simulator (NASim)) can be applied in a virtual machine range and complete the penetration task in a small-scale enterprise-level network scenario.
-
Setup a enterprise-level virtual machine network with a variety of virtual machines that has different operating systems.
-
Transfer/duplicate the virtual machine network to
NASimto create a AI training simulation environment. -
Train the AI in the NASim simulation environment to use using our proposed reinforcement learning algorithm -- CLAP.
-
Using this script (
run.py), which automatically executes the RL agent's discovered optimal RL strategy, complete the penetration task in the virtual machine range.
We build up the vitrual machine network following 0xBEN's tutorial:
https://benheater.com/building-a-security-lab-in-virtualbox/.
The configuration and target machines are described as follows:
-
Attacker
- Kali Linux
- IP-Address: 10.0.0.14
-
Victim 01
- Metasploitable 2
- IP-Address: 10.6.6.13
-
Victim 02
- Metasploitable 2
- IP-Address: 10.80.80.5
-
The penetration task's goal is to gain root access to the target node.
-
The agent's available actions are "scan," "exploit," and "privilege escalation."
The virtual machine network can be translated into NASim configurations, as shown in the table below.
| NASim | Virtual Machine Network | Subnet ID | Hosts IDs |
|---|---|---|---|
| External Network | kali | 0 | (0,0) |
| DMZ | pfSense Router | 1 | (1,0) |
| Sensitive Subnet | Isolated Network | 2 | (2,0),(2,1),(2,2)* |
| User Subnet | Windows AD | 3 | (3,0),(3,1),(3,2) |
We use our previously developed RL algorithim proposed in "Behaviour-Diverse Automatic Penetration Testing: A Curiosity-Driven Multi-Objective Deep Reinforcement Learning Approach" to train a AI agent. Under this scenario its optimal policy can be interpreted into the following sequence of actions:
- 'SubnetScan'Host "(0, 0)",
- 'Exploit' Host "(1, 0)",
- 'Exploit' Host "(2, 2)",
- 'Exploit' Host "(3, 1)",
- 'PrivEsc' Host "(3, 1)",
However, to make sure such optimal attack path can actually works in the VM network, we have to add some scans.
python-nmappymetasploit3- pyfiglet
- pandas
After setup the virtual machine network, clone this repo to the kali machine:
git clone https://github.com/yyzpiero/auto-pentesting-vm-range.gitafter install the required packages, run the python script:
python run.pyPlease note that, for ssh brute force we provide a neat password file with know credentials on
metasploitable 2
The following example depicts the entire automated process of penetrating the Virtual Range System, starting from the Kali Linux attacker host.

- Windows Hosts Exploitation
- PrivEsc