-
Notifications
You must be signed in to change notification settings - Fork 170
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Merge pull request #109 from inwafula/main
Added new KQL custom plugin and image folder-Anomaly detection
- Loading branch information
Showing
8 changed files
with
788 additions
and
791 deletions.
There are no files selected for viewing
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
1,156 changes: 578 additions & 578 deletions
1,156
Logic Apps/Get-CfS-Risky-Incidents-Report/azuredeploy.json
Large diffs are not rendered by default.
Oops, something went wrong.
34 changes: 17 additions & 17 deletions
34
Plugins/Community Based Plugins/AbuseIPDB/API-GetAbuseIPDBIP.yaml
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,17 +1,17 @@ | ||
| Descriptor: | ||
| Name: Get AbuseIPDB IP Address Information | ||
| DisplayName: Get AbuseIPDB IP Address Information | ||
| Description: Get detailed IP Address reputation information from AbuseIPDB | ||
| SupportedAuthTypes: | ||
| - ApiKey | ||
| Authorization: | ||
| Type: APIKey | ||
| Key: Key | ||
| Location: Header | ||
| AuthScheme: '' | ||
|
|
||
| SkillGroups: | ||
| - Format: API | ||
| Settings: | ||
| OpenApiSpecUrl: https://raw.githubusercontent.com/Azure/Copilot-For-Security/main/Plugins/Community%20Based%20Plugins/AbuseIPDB/OpenAPI/API-GetAbuseIPDBIP-OAPI.yaml | ||
|
|
||
| Descriptor: | ||
| Name: Get AbuseIPDB IP Address Information | ||
| DisplayName: Get AbuseIPDB IP Address Information | ||
| Description: Get detailed IP Address reputation information from AbuseIPDB | ||
| SupportedAuthTypes: | ||
| - ApiKey | ||
| Authorization: | ||
| Type: APIKey | ||
| Key: Key | ||
| Location: Header | ||
| AuthScheme: '' | ||
|
|
||
| SkillGroups: | ||
| - Format: API | ||
| Settings: | ||
| OpenApiSpecUrl: https://raw.githubusercontent.com/Azure/Copilot-For-Security/main/Plugins/Community%20Based%20Plugins/AbuseIPDB/OpenAPI/API-GetAbuseIPDBIP-OAPI.yaml | ||
|
|
129 changes: 0 additions & 129 deletions
129
...Ops-CustomPlugin/GitHubAdvancedSecurityForAzureDevOpsPlugin-Management-Specification.yaml
This file was deleted.
Oops, something went wrong.
96 changes: 96 additions & 0 deletions
96
...ustom Plugin Scenarios/Anomalous App and Admin Activity/AnomalousAppandAdminActivity.yaml
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,96 @@ | ||
| Descriptor: | ||
| Name: AnomalousAppandAdminUserActivity | ||
| DisplayName: Anomalous Application and Admin User Activity | ||
| Description: Uses UEBA normalized Insights in Sentinel UEBA to identify Applications observed for the first time in the tenant over the last 30 days. It applies to profiled activities across ARM, Azure sign-in, and audit logs | ||
| Settings: | ||
| - Name: TenantId | ||
| Required: true | ||
| - Name: WorkspaceName | ||
| Required: true | ||
| - Name: SubscriptionId | ||
| Required: true | ||
| - Name: ResourceGroupName | ||
| Required: true | ||
| SupportedAuthTypes: | ||
| - None | ||
|
|
||
| SkillGroups: | ||
| - Format: KQL | ||
| Skills: | ||
| - Name: AnomalousAppActivity | ||
| DisplayName: Anomalous application activity | ||
| Description: Uses Sentinel UEBA to identify unsual or anomalous activities such as first time a user used an app, an uncommonly used app, an app uncommonly used among user peers, an app that is observed in a tenant for the first time or an app that is uncommonly used in the tenant | ||
| Inputs: | ||
| - Name: fromDateTime | ||
| Description: The start of the lookback window | ||
| Required: true | ||
| - Name: toDateTime | ||
| Description: The end of the lookback window | ||
| Required: true | ||
| - Name: InvestiGationPriority | ||
| Description: Calculated priority for investigation between 1 and 10 | ||
| Required: false | ||
| Settings: | ||
| Target: Sentinel | ||
| # The ID of the AAD Organization that the Sentinel workspace is in. | ||
| TenantId: '{{TenantId}}' | ||
| # The id of the Azure Subscription that the Sentinel workspace is in. | ||
| SubscriptionId: '{{SubscriptionId}}' | ||
| # The name of the Resource Group that the Sentinel workspace is in. | ||
| ResourceGroupName: '{{ResourceGroupName}}' | ||
| # The name of the Sentinel workspace. | ||
| WorkspaceName: '{{WorkspaceName}}' | ||
| Template: |- | ||
| let fromDateTime=datetime('{{fromDateTime}}'); | ||
| let toDateTime=datetime('{{toDateTime}}'); | ||
| BehaviorAnalytics | ||
| | project-away TenantId, Type, SourceRecordId, EventSource, TimeProcessed | ||
| | where InvestigationPriority > 5 | ||
| | where ActivityInsights.FirstTimeUserUsedApp == true or | ||
| ActivityInsights.AppUncommonlyUsedByUser == true or | ||
| ActivityInsights.AppUncommonlyUsedAmongPeers == true or | ||
| ActivityInsights.FirstTimeAppObservedInTenant == true or | ||
| ActivityInsights.AppUncommonlyUsedInTenant == true | ||
| - Name: AnomalousAdminActions | ||
| DisplayName: Anomalous administrative actions performed by user | ||
| Description: Uses Sentinel UEBA to identify Users performing activities that are performed for the first time, uncommon by the user, uncommon among the user's peers, uncommon in the tenant, from an uncommon country or a user connecting from a country seen for the first time, or user accessing a resource for the first time or accessing a resource that is uncommon among their peers | ||
| Inputs: | ||
| - Name: fromDateTime | ||
| Description: The start of the lookback window | ||
| Required: true | ||
| - Name: toDateTime | ||
| Description: The end of the lookback window | ||
| Required: true | ||
| - Name: InvestiGationPriority | ||
| Description: Calculated priority for investigation between 1 and 10 | ||
| Required: false | ||
| Settings: | ||
| Target: Sentinel | ||
| # The ID of the Entra ID Organization that the Sentinel workspace is in. | ||
| TenantId: '{{TenantId}}' | ||
| # The id of the Azure Subscription that the Sentinel workspace is in. | ||
| SubscriptionId: '{{SubscriptionId}}' | ||
| # The name of the Resource Group that the Sentinel workspace is in. | ||
| ResourceGroupName: '{{ResourceGroupName}}' | ||
| # The name of the Sentinel workspace. | ||
| WorkspaceName: '{{WorkspaceName}}' | ||
| Template: |- | ||
| let fromDateTime=datetime('{{fromDateTime}}'); | ||
| let toDateTime=datetime('{{toDateTime}}'); | ||
| BehaviorAnalytics | ||
| | where datetime_utc_to_local(TimeGenerated, "US/Eastern") between ( fromDateTime .. toDateTime ) | ||
| | project-away TenantId, Type, SourceRecordId, EventSource, TimeProcessed | ||
| | where ActivityType =~ "Administrative" | ||
| | where isnotempty(UserName) | ||
| | where ActivityInsights.FirstTimeUserPerformedAction == true or | ||
| ActivityInsights.FirstTimeActionPerformedInTenant == true or | ||
| ActivityInsights.ActionUncommonlyPerformedByUser == true or | ||
| ActivityInsights.ActionUncommonlyPerformedAmongPeers == true or | ||
| ActivityInsights.FirstTimeUserAccessedResource == true or | ||
| ActivityInsights.CountryUncommonlyConnectedFromByUser == true or | ||
| ActivityInsights.IsDormantAccount == true or | ||
| ActivityInsights.IsLocalAdmin == true or | ||
| ActivityInsights.IsNewAccount == true | ||
30 changes: 30 additions & 0 deletions
30
...oft Sentinel Custom Plugin Scenarios/Anomalous App and Admin Activity/Readme.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,30 @@ | ||
| # Copilot for Security Custom KQL Plugin - Detect Anomalous App and User Activty using Microsoft Sentinel UEBA Insights | ||
|
|
||
| #### Copilot for Security Plugin to that brings in data from Microsoft Sentinel UEBA insights focussed on anomalies related to Applications and administrative user activity. For details refer to this blog: | ||
|
|
||
| ### Pre-requisites | ||
|
|
||
| * [Copilot for Security Enabled](https://learn.microsoft.com/en-us/security-copilot/get-started-security-copilot#onboarding-to-microsoft-security-copilot) | ||
| * [Access to upload custom plugins](https://learn.microsoft.com/en-us/security-copilot/manage-plugins?tabs=securitycopilotplugin#managing-custom-plugins) | ||
| * [Microsoft Sentinel Workspace](https://learn.microsoft.com/en-us/azure/sentinel/quickstart-onboard) created. | ||
| * [Microsoft Sentinel UEBA enabled](https://learn.microsoft.com/en-us/azure/sentinel/identify-threats-with-entity-behavior-analytics) | ||
| * Parameters for KQL Plugin - Microsoft Sentinel Workspace Name, Subscription ID, Resource Group Name and Entra Tenant ID | ||
|
|
||
| ### Instructions | ||
| #### Upload the Custom Plugin | ||
|
|
||
| 1. Obtain the file [AnomalousAppandUserActivity.yaml](https://github.com/Azure/Copilot-For-Security/blob/main/Plugins/Community%20Based%20Plugins/Microsoft%20Sentinel%20Custom%20Plugin%20Scenarios/Anomalous%20App%20and%20Admin%20Activity/AnomalousAppandAdminActivity.yaml) from this directory. | ||
| 2. Modify the KQL query as needed to suit your specific requirements. One such edit might be your Time Zone as converted in this line: | where datetime_utc_to_local(TimeGenerated, "US/Eastern") between ( fromDateTime .. toDateTime ). | ||
|
|
||
|
|
||
| 3. [Upload the custom plugin](https://learn.microsoft.com/en-us/security-copilot/manage-plugins?tabs=securitycopilotplugin#add-custom-plugins) and enter your Tenant ID, Subscription ID, Workspace name, Resource group that hosts your Sentinel worksapce in the resulting dialog box. Verify that the plugin is activated. | ||
|
|
||
| 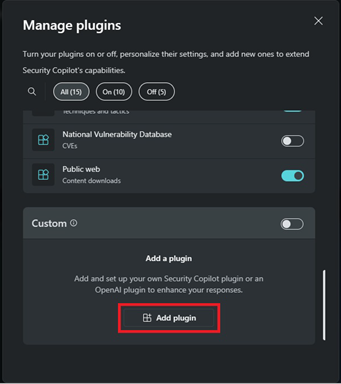 | ||
|
|
||
|
|
||
| 4. [Enter your workspace details in the Copilot for Security UI](https://github.com/Azure/Copilot-For-Security/blob/main/Images/KQL Plugin images/Workspacedetails.png) | ||
|
|
||
|
|
||
| ### Plugin Utilization | ||
|
|
||
| Refer to the blog in this link: |
Oops, something went wrong.