-
Notifications
You must be signed in to change notification settings - Fork 3
Reading List
Harlan T Wood edited this page Jun 13, 2017
·
14 revisions
- What are capabilities
- E in a walnut
- "The object reference graph becomes the access graph."
- Capability myths demolished 1
- Capability myths demolished 2
- An Ode to the Granovetter diagram
- Capability Oriented Programming
- Lambda calculus
- Lambda Calculus - Computerphile
- Modular arithmetic (essential for many, many crypto schemes)
- More in-depth mathematics needed for crypto:
- Finite field (Our focus: prime-order fields)
-
The mathematical groups most often used for Schnorr signatures
- Subgroups of cyclic groups (Further background on why Schnorr groups are mathematically sound for the desired properties)
- Terse description of a Schnorr signature's mathematics
- Security considerations of Schnorr signatures (many parts apply to many other crypto schemes):
- Why it's so difficult to break Schnorr signatures (and many other crypto schemes)
- Why we must use prime-order groups
- Why we need the primes to be large and why reusing primes excessively is bad
- Most-efficient publicly known ways to solve prime-order-group discrete logarithm problems: Pollard's rho algorithm for logarithms and Index calculus algorithm
- Legality of export from the U.S.A.
- Zero-knowledge proofs
- Multisig: see Signature Options
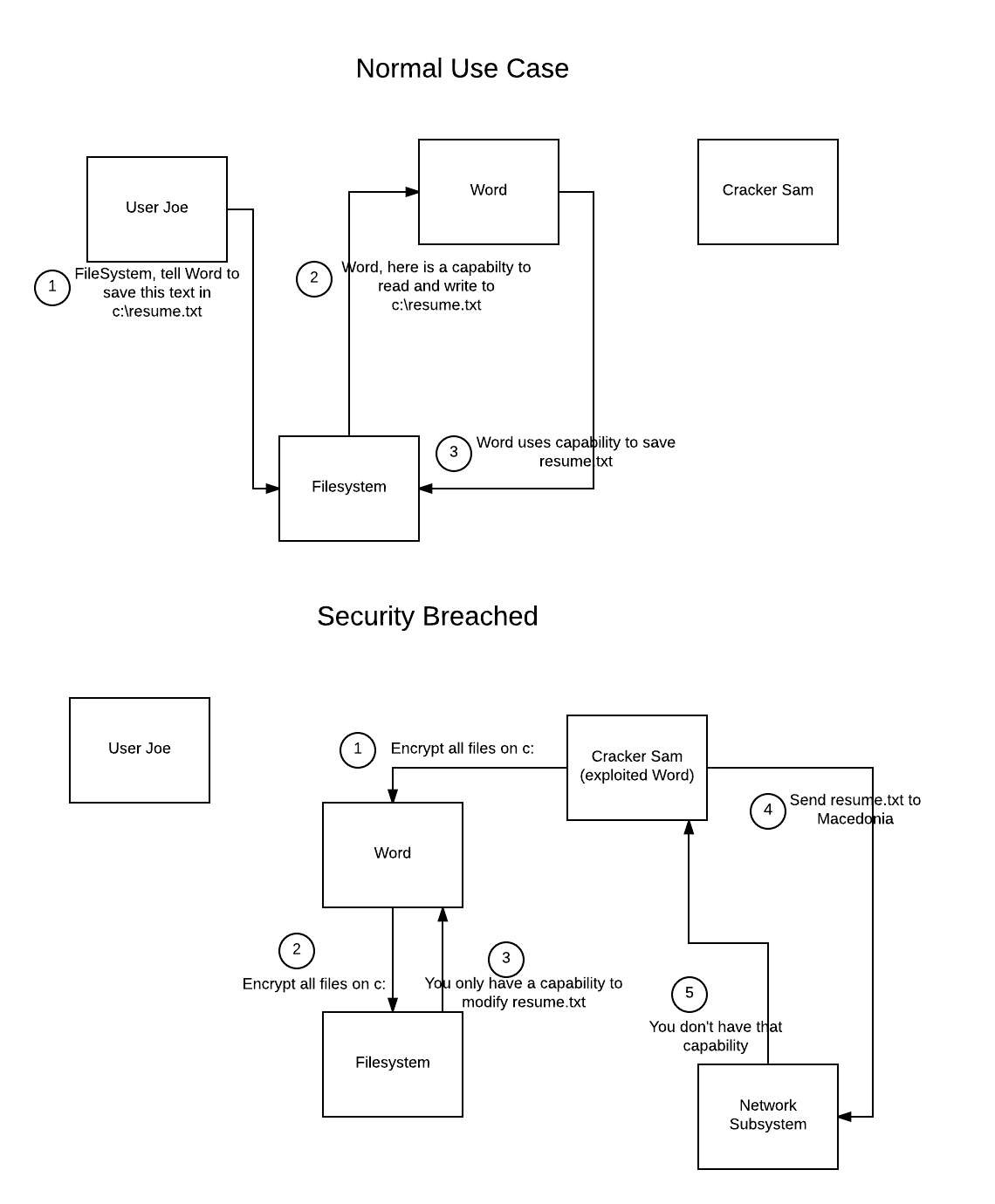
Breach in an ACL oriented system:
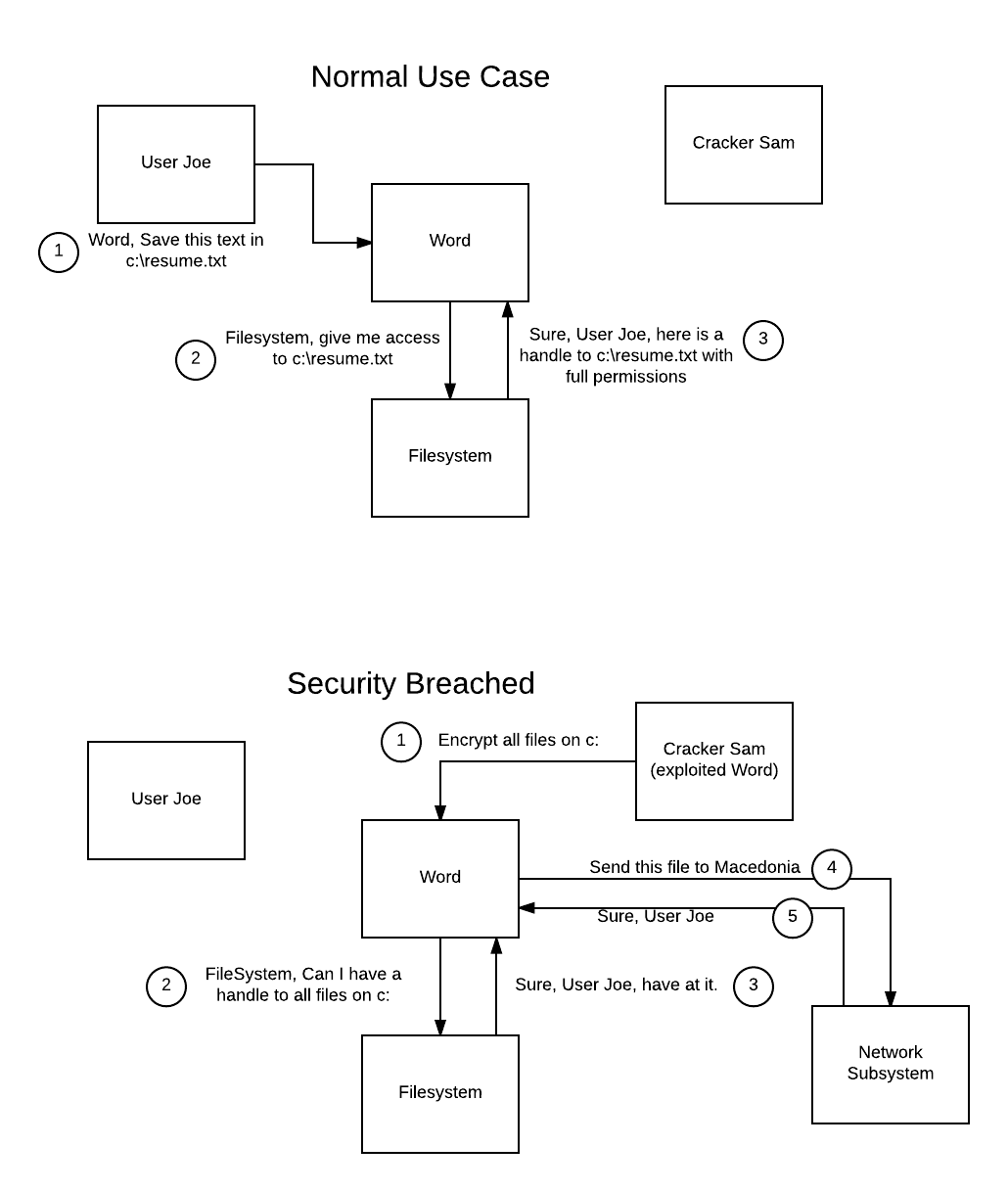
Breach in a Capabilities Oriented system: