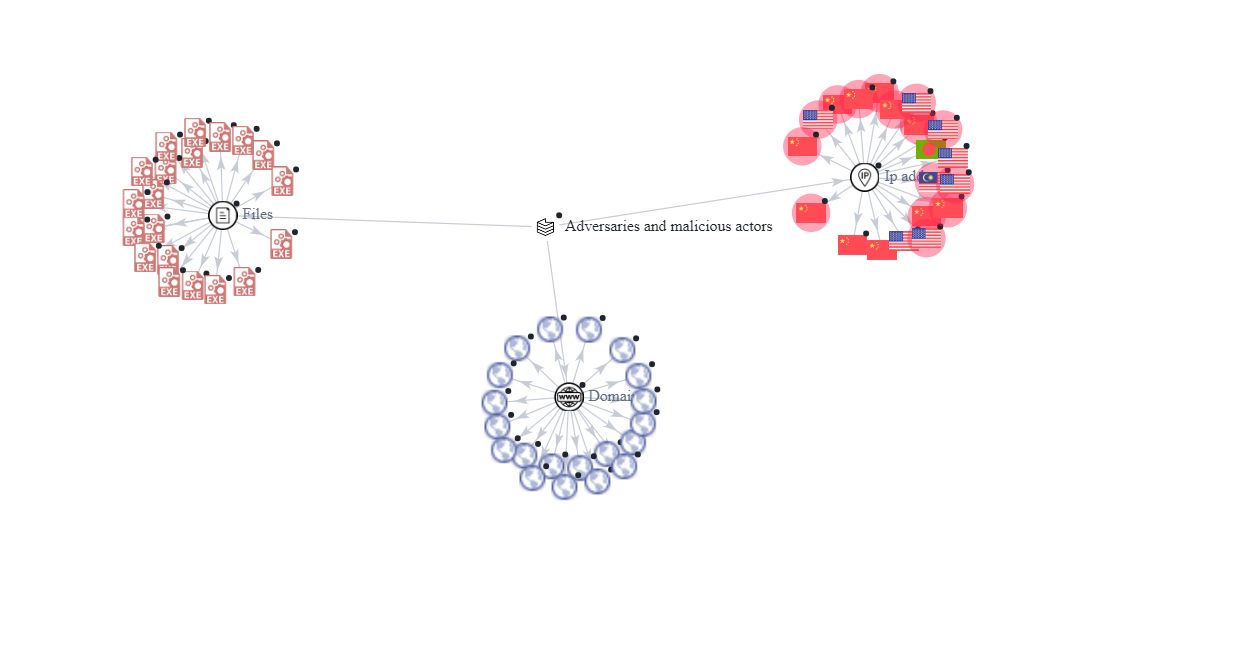
List of aggregated and summarized files from a network of global honeypots that belong to a personal investigation.
Files:
MaliciousIP.txt- List of malicious IPs that have been successful in a honeypot attackC2_BruteRatel.txt- List of adversary Command & Control from Brute Ratel frameworkC2_CobaltStrikeBeacon.txt- List of adversary Command & Control from Cobalt Strike BeaconsC2_Metasploit.txt- List of adversary Command & Control from Metasploit FrameworkC2_Covenant.txt- List of adversary Command & Control from CovenantC2_Mythic.txt- List of adversary Command & Control from Mythic FrameworkC2_All.txt- Contains all the CSV files grouped in a single fileC2_statistics_All.txt- Contains the statistics of the malicious IPs of the entire C2_All.csv file in the last 24 hoursC2_GeoLocation.txt- Geolocations of the malicious IPs of the entire C2_All.csv file in the last 24 hoursMalicious_IP_C2_All.txt- Contains the malicious IPs of the adversaries of all the C2_ files in the last 24 hourslast24hours_Malwarehashes.txt- Malicious hashes obtained in the last 24 hoursC2_Deimos- List of adversary Command & Control from Deimos FraeworkC2_Panda- List of adversary Command & ControlC2_PoweSploit- List of adversary Command & ControlC2_Posh- List of adversary Command & Control Framework
Files directory maps:
attackerconnection.png- Graph of interest of the attacks received towards the honey located in Ukraine (coming soon)attackersmap.png- Graph that obtains the origin of the attacks (coming soon)
Files directory raw_config_C2:
C2_BruteRatel.json- List of raw formatC2_CobaltStrikeBeacon.json- List of raw formatC2_Metasploit.json- List of raw formatC2_Covenant.json- List of raw formatC2_Mythic.json- List of raw formatC2_Deimos.json- List of raw formatC2_Panda.json- List of raw formatC2_PowerSploit.json- List of raw formatC2_Posh.json- List of raw format
Notes:
- All files are updated every hour except Brute rate, Covenant, Mythic, CobaltStrike, Metasploit, Deimos, Panda, PowerSploit, Posh and C2_All.csv files that are updated daily at 7:25 a.m.(CET)
- The honeypot network is distributed in most countries of the world. Especially in those countries at war or with a situation of diplomatic crisis between power zones.
- Most of the honeypots are highly interactive and many of them pretend to be from departmental governments, technology industry, aerospace and military.
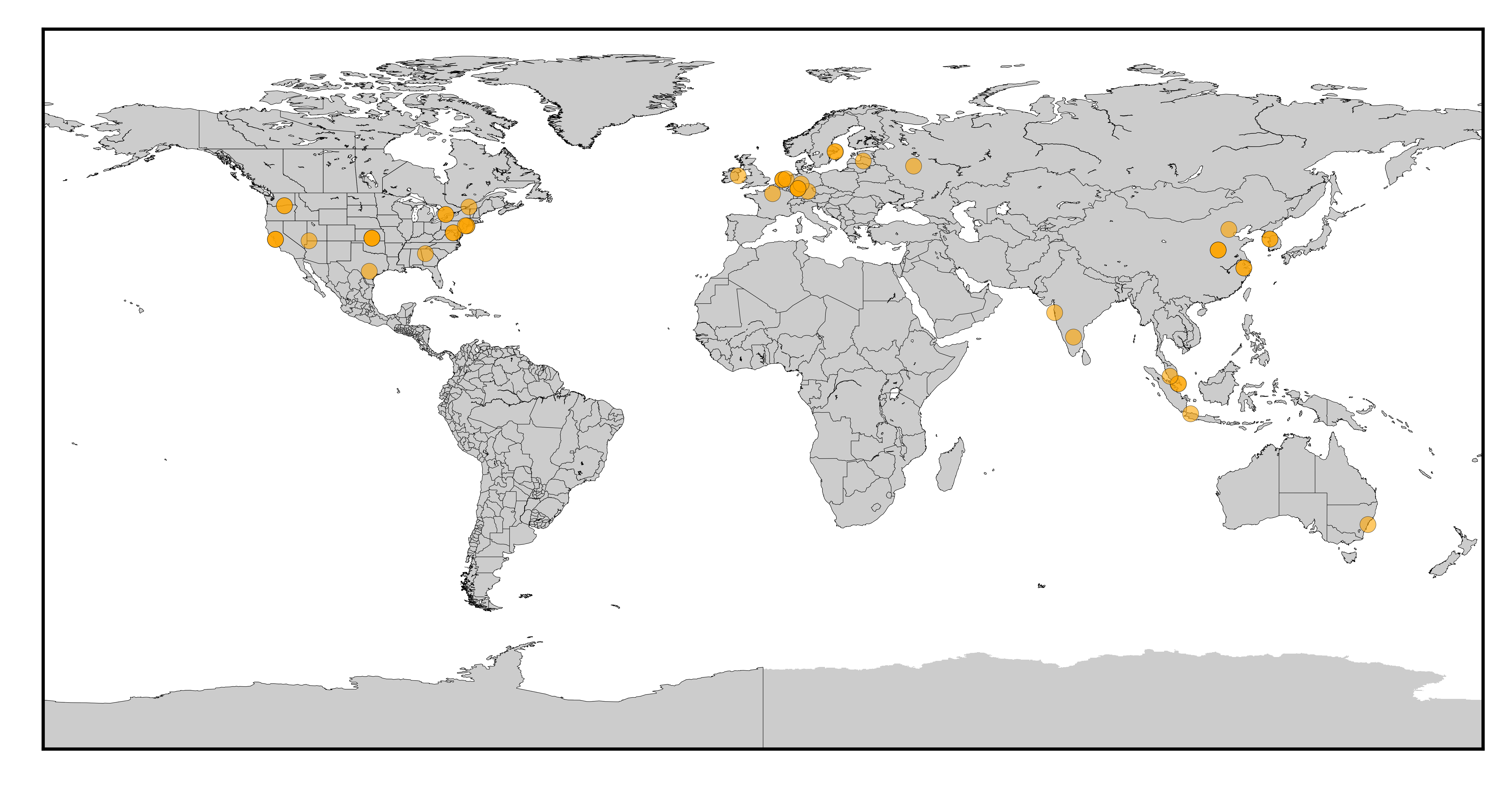
Map of the origins of the command & control
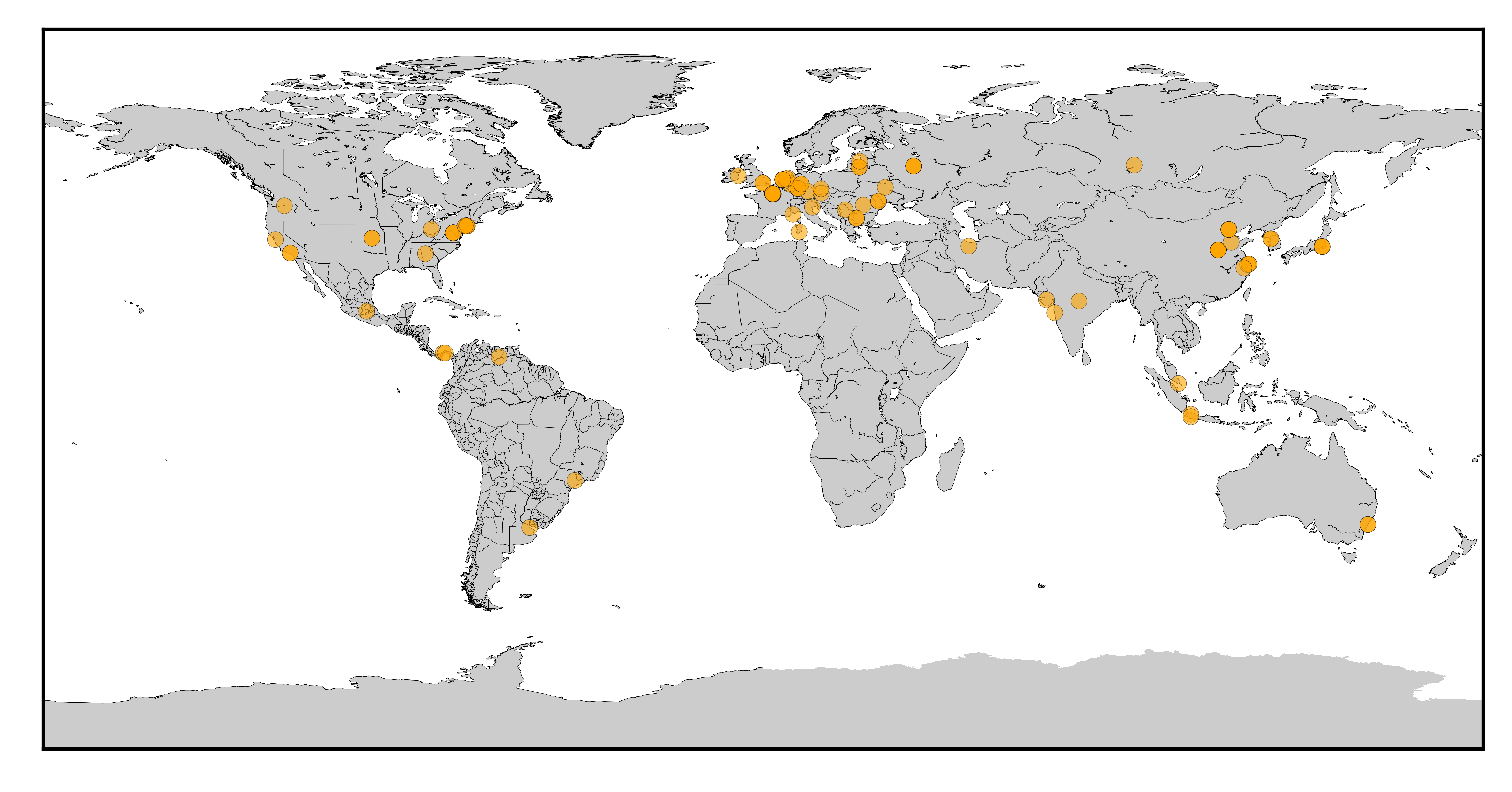
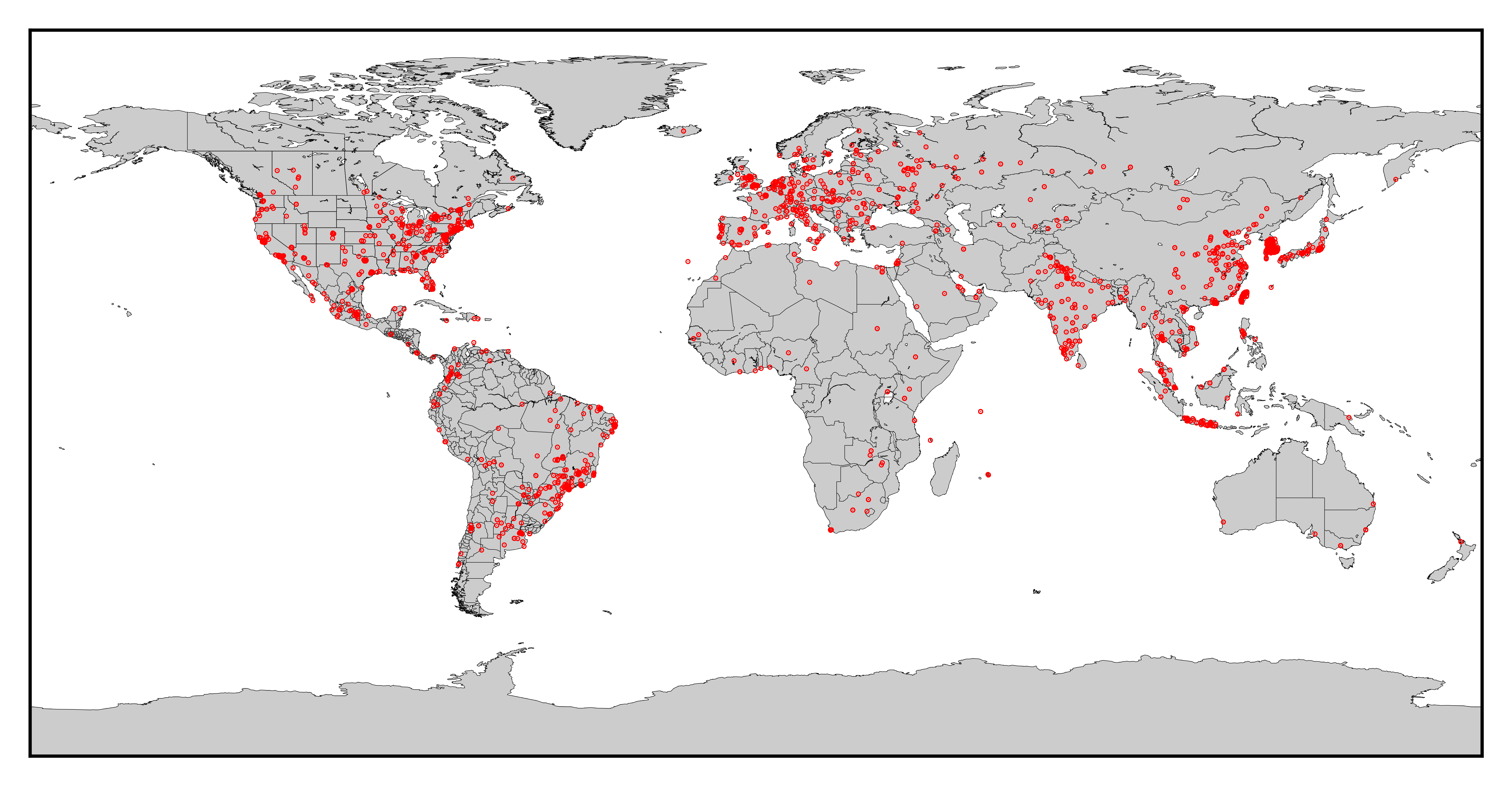 Map of the origins of the attacks since January 2023
Map of the origins of the attacks since January 2023
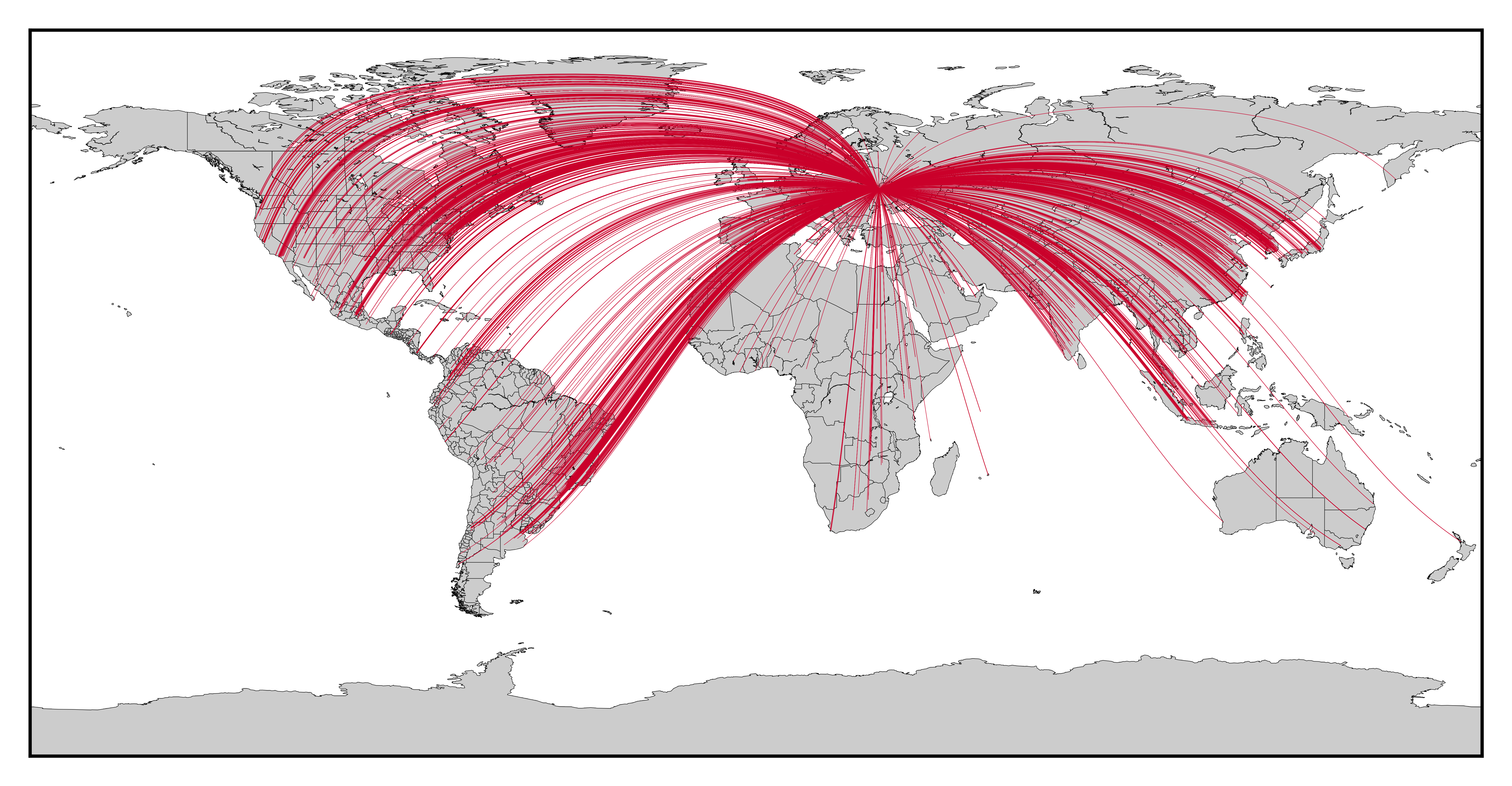 Representative map of attacks received on Ukraine since January 2023
Representative map of attacks received on Ukraine since January 2023
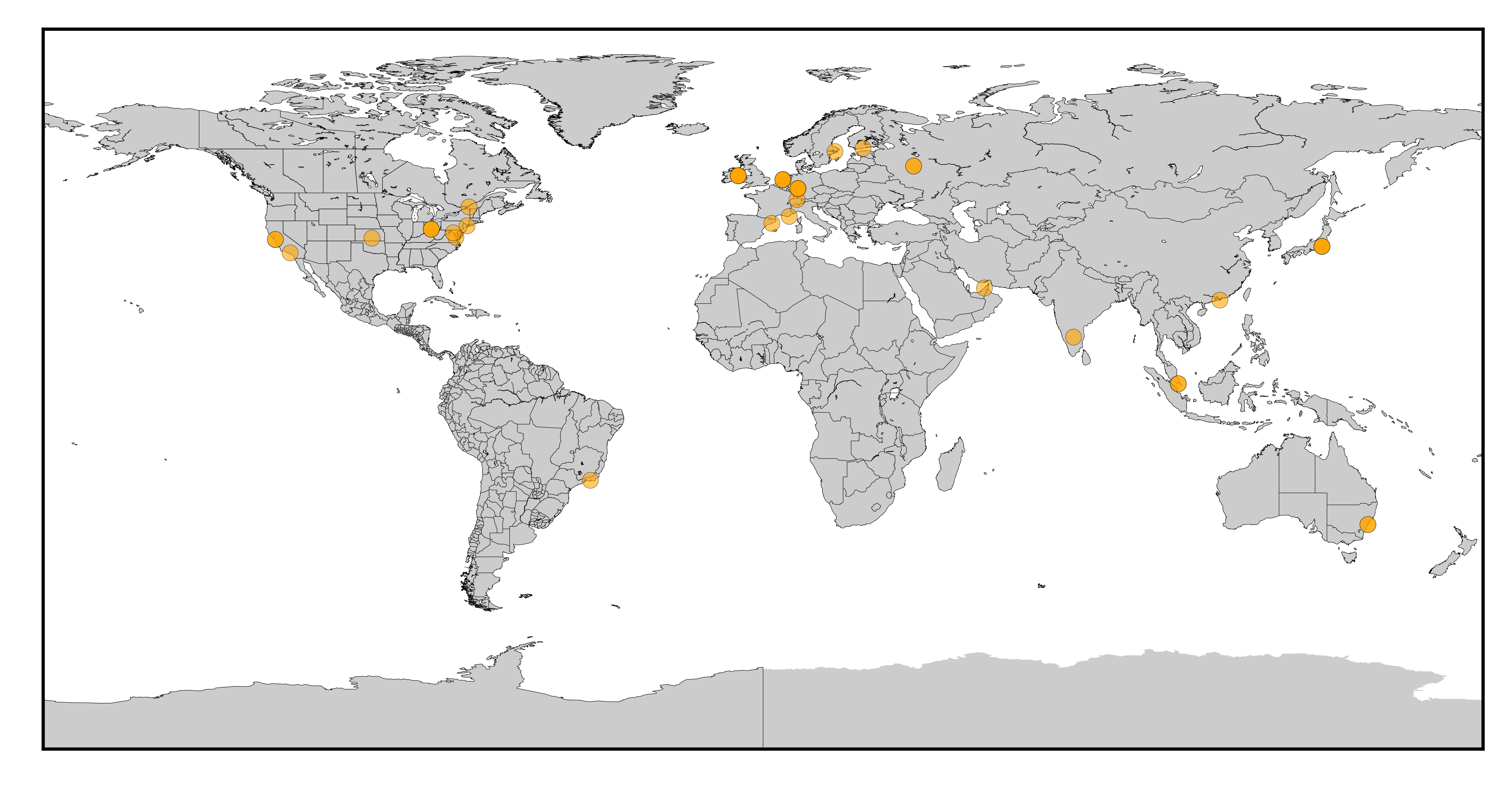 Representative map of BrutelRatel attack origins
Representative map of BrutelRatel attack origins
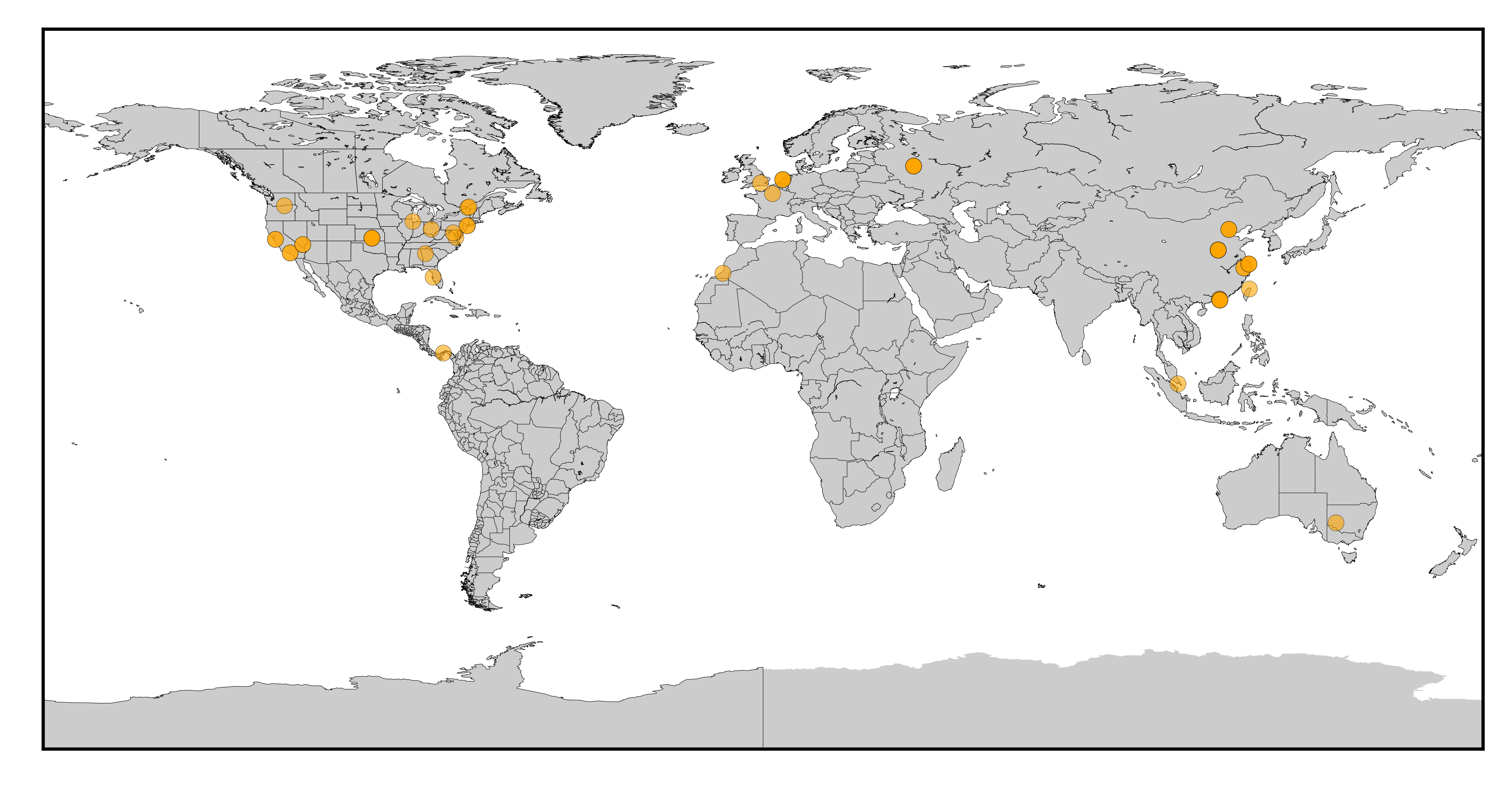 Representative map of CobaltStrike attack origins
Representative map of CobaltStrike attack origins
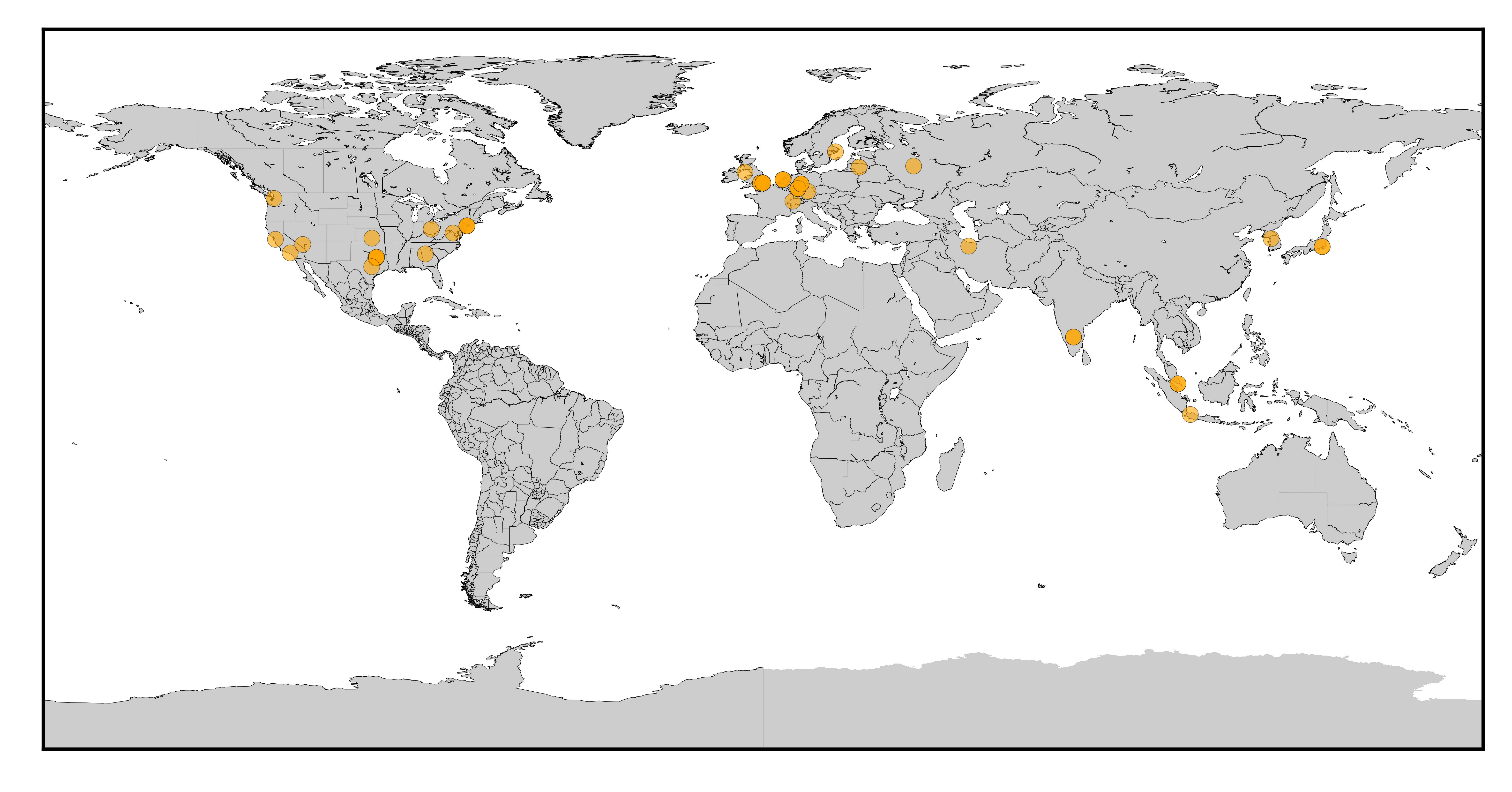 Representative map of Covenant attack origins
Representative map of Covenant attack origins