Images are based on Ubuntu 22 or Alpine 3.21. Unfortunately, Alpine repository does not include a cloud driver for bacula storage. Bacula community repository for Ubuntu, on the other hand, does have a cloud driver for bacula storage. Therefore I had to create two docker images. Ubuntu docker image does have a cloud driver for bacula storage.
| pull | size ubuntu | size alpine | version ubuntu | version alpine | platform |
|---|---|---|---|---|---|
 |
 |
 |
 |
 |
 |
| ALpine version | Ubuntu version | Bacularis version |
|---|---|---|
 |
 |
 |
Bacula is a set of Open Source, computer programs that permit you to manage backup, recovery, and verification of computer data across a network of computers.
Bacularis is a web interface to configure, manage and monitor Bacula backup environment. It is a complete solution for setting up backup jobs, doing restore data, managing tape or disk volumes in local and remote storage, work with backup clients, and doing daily administrative work with backup.
Bacula linux binaries Deb / Rpm can be found on Bacula website. To access these binaries, you will need an access key, which will be provided when you complete a simple registration.
- Install bacula client on Debian / Ubuntu
apt-get update
apt-get install apt-transport-http
# Import GPG key
cd /tmp
wget https://www.bacula.org/downloads/Bacula-4096-Distribution-Verification-key.asc
apt-key add Bacula-4096-Distribution-Verification-key.asc
rm Bacula-4096-Distribution-Verification-key.asc
### Debian - create repo file
ACCESS_KEY=MyAccessKey
BACULA_VERSION=13.0.4
DEBIAN_VERSION=bullseye
cat > /etc/apt/sources.list.d/Bacula-Community.list << EOL
# Bacula Community
deb https://www.bacula.org/packages/${ACCESS_KEY}/debs/${BACULA_VERSION} ${DEBIAN_VERSION} main
EOL
### Ubuntu - create repo file
ACCESS_KEY=MyAccessKey
BACULA_VERSION=13.0.4
DEBIAN_VERSION=jammy
cat > /etc/apt/sources.list.d/Bacula-Community.list << EOL
# Bacula Community
deb https://www.bacula.org/packages/${ACCESS_KEY}/debs/${BACULA_VERSION} ${DEBIAN_VERSION} main
EOL
# install bacula client
apt-get update
apt-get install bacula-client
systemctl enable --now bacula-fd
systemctl status bacula-fd- Install bacula client on CentOS / Redhat / Rocky /Oracle
# Import GPG key
cd /tmp
wget https://www.bacula.org/downloads/Bacula-4096-Distribution-Verification-key.asc
rpm --import Bacula-4096-Distribution-Verification-key.asc
rm Bacula-4096-Distribution-Verification-key.asc
# Create dnf / yum - repo file
ACCESS_KEY=MyAccessKey
BACULA_VERSION=13.0.4
EL_VERSION=el8
cat > /etc/yum.repos.d/Bacula.repo << EOL
[Bacula-Community]
name=CentOS - Bacula - Community
baseurl=https://www.bacula.org/packages/${ACCESS_KEY}/rpms/${BACULA_VERSION}/${EL_VERSION}/x86_64/
enabled=1
protect=0
gpgcheck=1
gpgkey=https://www.bacula.org/downloads/Bacula-4096-Distribution-Verification-key.asc
EOL
# install bacula client
dnf install bacula-client
systemctl enable --now bacula-fd
systemctl status bacula-fdBacula windows binaries can be found on Bacula website.
- Create folders, set permissions
# create folders
mkdir -p /opt/bacularis/data/{bacularis,bacula,pgsql}
mkdir -p /opt/bacularis/data/bacularis/www/bacularis-api/API/{Config,Logs}
mkdir -p /opt/bacularis/data/bacularis/www/bacularis-web/Web/{Config,Logs}
mkdir -p /opt/bacularis/data/bacula/config/etc
mkdir -p /opt/bacularis/data/pgsql/{data,socket}
mkdir -p /opt/bacularis/data/smtp/secret
tree -d -L 6 /opt/bacularis
# create bacula storage folder
mkdir -p /mnt/USB_NFS_PVE01/bacula/archive
# set rights: 101 - bacula user uid; 26 - tape group gid
chown 101:102 /opt/bacularis/data/bacula/config/etc
chown 101:26 /mnt/USB_NFS_PVE01/bacula/archive- Create docker-compose.yml
or - Download all files below
cd /opt/bacularis
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/docker-compose.yml
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/docker-compose.override.yml
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/.env
# show used subnets
cd /opt/bacularis && grep -r SUBNET /opt/*- Customize variables in all files
- Generate
adminuserpasswordhere. You need both passwords decrypt and encrypted
# generate admin password
pwgen -1cnsB 20 5
# Example
Username: admin
Password decrypt: N04X1UYYbZ2J69sAYLb0N04
Password encrypted: $apr1$o2vlak5p$saFj/wl/MeGxQysvc462R1
- Customize the file
docker-compose.override.ymlif you use trafik - Run docker container
cd /opt/bacularis
docker-compose up -d
docker-compose ps
docker-compose logs
docker-compose logs bacularis- check if all services in container are running
dcexec bacularis bash
ss -tln
exit- Adjust postgres database access rights file
pg_hba.conf
# show IP Address of bacula-db
CONTAINER_NAME=$(docker ps --format 'table {{.ID}}\t{{.Names}}' |grep bacula-db |awk '{print $1}')
dcexec bacula-db cat /etc/hosts |grep ${CONTAINER_NAME}
# change pg_hba.conf
vim /opt/bacularis/data/pgsql/data/pg_hba.conf
---------------
from
...
# IPv4 local connections:
host all all 127.0.0.1/32 trust
...
to
...
# IPv4 local connections:
host all all 127.0.0.1/32 trust
host all all 172.26.2.0/24 trust
...
-------------- Change var
DB_INIT=truetoDB_INIT=false
cd /opt/bacularis && vim docker-compose.yml
--------------
environment:
from
...
- DB_INIT=true
...
to
...
- DB_INIT=false
...
-------------Before restarting the Docker Stack after the above changes, the access rights to the path /mnt/USB_NFS_PVE01/bacula/archive must be checked again and corrected if necessary.
# Check rights and correct if necessary
ls -la /mnt/USB_NFS_PVE01/bacula/
chown -R 101:26 /mnt/USB_NFS_PVE01/bacula/archive
ls -la /mnt/USB_NFS_PVE01/bacula/
# Docker Stack restart
cd /opt/bacularis
docker-compose down && docker-compose up -dURL: https://bacularis.mydomain.de
User: admin
Password: Is in the .env file- Bacularis docker container
| Variable | Value | Description |
|---|---|---|
| TZ | Europe/Berlin | Time zone |
| DB_INIT | true or false | true - required for DB init only (first run) |
| DB_UPDATE | false or true | true - required for DB update only |
| DB_HOST | bacula-db | PostgreSQL db host name |
| DB_PORT | 5432 | PostgreSQL db port |
| DB_NAME | bacula | bacula database name |
| DB_USER | bacula | bacula user name |
| DB_PASSWORD | MyDBPassword | password use to access to the bareos database |
| DB_ADMIN_USER | postgres | PostgreSQL root user name (required for DB init only) |
| DB_ADMIN_PASSWORD | MyDBAdminPassword | Password for PostgreSQL root user (required for DB init only) |
| BUILD_DAEMON_NAME | build-3-17-x86_64 | from alpine assigned bacula daemons name |
| DESIRED_DAEMON_NAME | bacula | desired name for bacula daemons |
| WEB_ADMIN_USER | admin | User name for bacula web interface |
| WEB_ADMIN_PASSWORD_DECRYPT | MyWebPassword | User password (decrypt) for bacula web interface |
| WEB_ADMIN_PASSWORD_ENCRYPTED | $apr1$1fvq6ki0$AScxxxx | User password (encrypted) for bacula web interface |
| SMTP_HOST | smtpd:8025 | docker container smtp service - name & port |
| ADMIN_MAIL | [email protected] | your email address |
| ADD_STORAGE_POOL | true or false | true - standard pool are replaced by Incremental, Differential and Full |
| DOCKER_HOST_IP | 192.168.2.10 | IP address of docker host |
| DOCKERDIR | /opt/bacularis | Docker container config and data folder |
| PORT_BACULARIS | 9097 | Bacula port for Web interface |
| PORT_STORAGE | 9103 | Bacula port for storage daemon: bacula-sd |
| PORT_DIRECTOR | 9101 | Bacula port for director daemon: bacula-dir |
| MEMORY_LIMIT | 1024 MB | PHP memory_limit in MB |
- bacula-db docker container
| Variable | Value | Description |
|---|---|---|
| TZ | Europe/Berlin | Time zone |
| DB_ADMIN_USER | postgres | PostgreSQL root user name (required for DB init only) |
| DB_ADMIN_PASSWORD | MyPostgresRootPassword | Password for PostgreSQL root user (required for DB init only) |
- smtpd docker container
| Variable | Value | Description |
|---|---|---|
| HOSTNAME_SMTP | bacularis.mydomain.de | hostname of smtp server |
| SMARTHOST | smtp.mydomain.de | smtp server FQDN |
| SMTP_USERNAME | [email protected] | smtp server user name |
| SMTP_PASSWORD | SmtpUserPassword | smtp server user password |
- Open
http://host.domain.com:9097or via traefikhttps://host.domain.comin your web browser then sign-in - Login with your
adminuser credentials (user:admin/ pass:<ADMIN_PASSWORD_DECRYPT>) - Check the
bacula directorsettings
- With docker
docker exec -it bacularis bconsole- With docker-compose
cd /opt/bacularis
docker-compose exec bacularis bconsole| Name | Type | Data |
|---|---|---|
| bacularis | CNAME | traefik-host.mydomain.de |
| bacula-dir | CNAME | docker-host.mydomain.de |
| bacula-sd | CNAME | docker-host.mydomain.de |
Ports that need to be opened in firewall.
| port | protocol | description |
|---|---|---|
| 9102 | TCP | For bacula-fd file daemon |
| 9103 | TCP | For bacula-sd storage daemon |
| 9097 | TCP | For Bacularis-APP without RP (Traefik) |
| 443 | TCP | For Bacularis-APP with RP (Traefik) |
- Example for CentOS/Oracle/Rocky Linux
firewall-cmd --permanent --zone=public --add-port=9102/tcp
firewall-cmd --permanent --zone=public --add-port=9103/tcp
firewall-cmd --permanent --zone=public --add-port=9097/tcp
firewall-cmd --permanent --zone=public --add-port=443/tcp
firewall-cmd --reload
firewall-cmd --list-all- If you have several companies / customers, it quickly becomes confusing when checking the emails. To avoid this, add the company/customer name to the
bacula-dirconfiguration. For example:
# customize variable
FIRMA=MyFirma
PATH_TO_BACULA_DIR=/opt/bacularis/data/bacula/config/etc/bacula-dir.conf
sed -i -e "s/Bacula:/Bacula ${FIRMA}:/" ${PATH_TO_BACULA_DIR}
cat ${PATH_TO_BACULA_DIR} |grep "Bacula ${FIRMA}:"
sed -i -e "s/Bacula daemon message/Bacula ${FIRMA} daemon message/" ${PATH_TO_BACULA_DIR}
cat ${PATH_TO_BACULA_DIR} |grep "Bacula ${FIRMA} daemon message" Exim mail relay is a lightweight Docker image, based on the official Alpine image. You can see the documentation for this here
You can create client config files automatically. For this you can find some scripts and templates on the repo. You load the files into a directory and start the bash scripts. Run scriptname -h / --help to see help.
-
SSH login to
bacula docker host -
Download files below in a directory
cd /tmp
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/1_create_new_bacula_client_linux--server_side_template.sh
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/2_create_new_bacula_client_linux--client_side_template.sh
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/bacula-dir_template.conf
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/bacula-dir_template_windows.conf
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/bacula-fd_template.conf
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/bconsole_template.conf
chmod u+x *.sh- To create configuration for Bacula
Linuxclient on server side, you need to pass two parameters to script 1, namelyclient nameandIP address - To create configuration for Bacula
Linuxclient on client side, you need to pass only one parametes to script 2, namelyclient name - The MD5
bacula clientpassword will be automatically created by the script - The
bacula-monpassword will be automatically read frombacula serverconfiguration. - When everything is ready, run the scripts to create bacula linux client config files. Here is an example:
CLIENT_NAME=srv01
IP_ADDRESS=$(ip addr show $(ip route | awk '/default/ {print $5}') |grep -w inet | awk '/inet/ {print $2}' | cut -d'/' -f1)
echo ${IP_ADDRESS}
./1_create_new_bacula_client_linux--server_side_template.sh -n ${CLIENT_NAME} -ip ${IP_ADDRESS}
./2_create_new_bacula_client_linux--client_side_template.sh -n ${CLIENT_NAME}- The created files can be found in the folder
config_files. The content of the filebacula-dir_srv01.confis added to the configuration filebacula-dir.confof thebacula server
# stop bacula docker stack
cd /opt/bacularis && docker-compose down
cd -
# add client config to bacula-dir
cat config_files/bacula-dir_srv01.conf >> /opt/bacularis/data/bacula/config/etc/bacula-dir.conf
# run bacula docker stack
cd /opt/bacularis && docker-compose up -d && docker-compose exec bacularis bash
# reread config
bconsole
reload
q
exit
cd -
- The created files
bacula-fd_srv01.confandbconsole_srv01.confmust be copied frombacula docker hostto client by folder/opt/bacula/etc - SSH to
bacula clienthost - Copy files
bacula-fd_srv01.confandbconsole_srv01.conffrombacula docker host
# on docker host - copy config files to bacula client host
scp config_files/bacula-fd_pve01.conf config_files/bconsole_pve01.conf user@bacula-client-ip:/tmp
ssh user@bacula-client-ip
cd /opt/bacula/etc
# create backup of old files
mv bacula-fd.conf bacula-fd.conf.back
mv bconsole.conf bconsole.conf.back
# move files
mv /tmp/bacula-fd_srv01.conf bacula-fd.conf
mv /tmp/bconsole_srv01.conf bconsole.conf
systemctl restart bacula-fd.service
# delete files
cd /tmp
rm -rf bacula-* bconsole_template.conf config_files *.sh
#
### if bacula client is running on the docker host, than
#
cd /opt/bacula/etc
mv bacula-fd.conf bacula-fd.conf.back
mv bconsole.conf bconsole.conf.back
\cp /tmp/config_files/bacula-fd_oraclel8.conf ./bacula-fd.conf
\cp /tmp/config_files/bconsole_oraclel8.conf ./bconsole.conf
systemctl restart bacula-fd.service
# delete files
cd /tmp
rm -rf bacula-* bconsole_template.conf config_files *.sh- Download files below in a directory
cd /tmp
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/3_create_new_bacula_client_windows--server_side_template.sh
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/bacula-dir_template_windows.conf
chmod u+x *.sh- To create configuration for Bacula
Windowsclient on server side, you need to pass two parameters to script 3, namelyclient nameandIP address - The MD5 Bacula client password is automatically created by the script
- When everything is ready, run the scripts to create bacula windows client config files. Here is an example:
cd /tmp
CLIENT_NAME=srv01
IP_ADDRESS="192.168.155.5"
./3_create_new_bacula_client_windows--server_side_template.sh -n ${CLIENT_NAME} -ip ${IP_ADDRESS}- The created files can be found in the folder
config_files. The content of the filebacula-dir_win-srv01.confis added to the configuration filebacula-dir.confof thebacula server
cd /tmp
cat config_files/bacula-dir_win-srv01.conf >> /opt/bacularis/data/bacula/config/etc/bacula-dir.conf
cd /opt/bacularis && docker-compose exec bacularis bash
bconsole
reload
q
exitFor the installation of Bacula Windows client you need the name of Bacula Director bacula-dir, MD5 password of bacula windows client and the ip address of docker host.
- You can read out MD5 bacula client password from created config file
bacula-dir_win-srv01.conf
cat config_files/bacula-dir_win-srv01.conf | sed -n '/Client {/,+4p' | grep -w Password |cut -f 2 -d '"'As a result comes something like this: [md5]607e60c2c1f4f859679fbe9d742b0c59
- You need the ip address of
docker host. This ip address is specified asbacula-dirip address. You can execute the following command ondocker hostto find out the ip address:
ip addr show $(ip route | awk '/default/ {print $5}') |grep -w inet | awk '/inet/ {print $2}' | cut -d'/' -f1As a result comes something like this: 192.168.155.15
- Download Bacula windows binaries from Bacula website
- Run bacula installation
- Fill in the data as in the picture
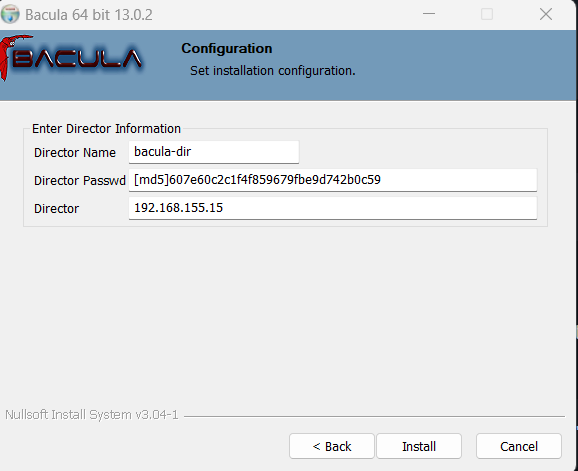
- Finish the installation
- Open the file
C:\Program Files\Bacula\bacula-fd.conf - Find the section
#
# List Directors who are permitted to contact this File daemon
#
Director {
Name = bacula-dir
Password = "Ck7WxwW8xfew45stslKdXoPGIAk+8QyB07tli92W1XWC" # Director must know this password
- Replace the password with the MD5 password from the client
#
# List Directors who are permitted to contact this File daemon
#
Director {
Name = bacula-dir
Password = "[md5]607e60c2c1f4f859679fbe9d742b0c59" # Director must know this password
- Restart Windows bacula daemon
- Windows firewall configuration - unblock ports 9102/TCP and 9103/TCP for incoming rules
- create docker-compose.override.ym
vim docker-compose.override.yml
---------------------------
version: "3.0"
networks:
proxy:
external: true
services:
bacularis:
labels:
- "traefik.enable=true"
- "traefik.docker.network=proxy"
- "traefik.http.routers.bacularis-secure.entrypoints=websecure"
- "traefik.http.routers.bacularis-secure.rule=Host(`$HOSTNAME0.$DOMAINNAME`)"
- "traefik.http.routers.bacularis-secure.service=bacularis"
#- "traefik.http.routers.bacularis-secure.tls.certresolver=produktion" # für eigene Zertifikate
- "traefik.http.routers.bacularis-secure.tls.options=modern@file"
- "traefik.http.routers.bacularis-secure.tls=true"
- "traefik.http.routers.bacularis-secure.middlewares=default-chain@file,rate-limit@file,authelia@file"
#- "traefik.http.routers.bacularis-secure.middlewares=default-chain@file,rate-limit@file"
- "traefik.http.services.bacularis.loadbalancer.sticky.cookie.httpOnly=true"
- "traefik.http.services.bacularis.loadbalancer.sticky.cookie.secure=true"
- "traefik.http.services.traefik.loadbalancer.server.port=${PORT}"
networks:
- proxyAuthelia docker container is located on the other host IP: 192.168.15.7/32 FQDN: auth.mydomain.de
Traefik docker container is located on the same host as bacularis docker container IP: 192.168.15.16/32
traefikcontainer: add middlewareautheliainto traefik config file
vim /opt/traefik/data/conf/traefik.yml
--------------------------------------
...
http:
...
middlewares:
...
authelia:
forwardAuth:
address: "http://auth.mydomain.de:9091/api/verify?rd=https://auth.mydomain.de/"
trustForwardHeader: true
...
# restart `Traefik` docker container
cd /opt/traefik && docker-compose up -dautheliacontainer: changedocker-compose.ymlas below
vim docker-compose.yml
--------------------
...
ports:
- 9091:9091
...autheliacontainer: add FQDN for bacularis webbacularis.mydomain.de
vim /opt/authelia/data/authelia/config/configuration.yml
--------------------------------------------------------
...
access_control:
default_policy: deny
rules:
- domain:
...
- domain: bacularis.mydomain.de
policy: one_factor
...
# restart `authelia` docker container
cd /opt/authelia && docker-compose up -dautheliacontainer host: add firewall rule for access toauth.mydomain.deport 9091 frombacularisdocker container hostIP: 192.168.15.16/32
firewall-cmd --permanent --zone=public --add-rich-rule='rule family="ipv4" port port="9091" protocol="tcp" source address="192.168.15.16/32" accept'
firewall-cmd --reload
firewall-cmd --zone=public --list-all- Download script below to the client
cd /opt/bacula/scripts/
wget https://raw.githubusercontent.com/johann8/bacularis-alpine/master/scripts/backup_mysql.sh
chmod a+x backup_mysql.sh
cd --
Start Bacularis-App and browse to: Director => Configure director => Job => Name => Edit => +Add => +Add Runscript block
-
Fill out as in the picture (Path to the location of the script)

-
Browse to: Director => Configure director => Fileset => Name => Edit => Include #1 +Add => +Add single file/directory
-
Fill out as in the picture (Var "DST" from script /var/backup/container/mysql)

For Postgres DB backup the Script autopostgresqlbackup is used. There is a docker container with this script. You can find a description and configaration example here.
- Here is an example of how to backup Postgres database in a docker container
# create backup destination
mkdir -p /var/backup/container/postgres
# Add to the docker container where the dostgres database runs
...
autopgbackup:
image: rogersik/autopostgresqlbackup:latest
container_name: autopgbackup
environment:
- DBHOST=${POSTGRES_HOST}
- USERNAME=${POSTGRES_USER}
- PASSWORD=${POSTGRES_PASSWORD}
- CRON_LOG_LEVEL=0 # Most verbose is 0, less verbose is 8
- CRON_SCHEDULE=50 22 * * * # valid cron specification
- LATEST=yes # Additionally keep a copy of the most recent backup in a seperate directory
volumes:
- /var/backup/container/postgres:/backups
- /etc/localtime:/etc/localtime:ro
depends_on:
- postgresdb
...- Start Bacularis-App and browse to: Director => Configure director => Fileset => Name => Edit => Include #1 +Add => +Add single file/directory
- Fill out as in the picture (Volume path fron docker-compose.yml: /var/backup/container/postgres)

Enjoy !