-
Notifications
You must be signed in to change notification settings - Fork 108
Network Security Overview
Context Part One: Network Security
Open Problems
Network growth in business context brings a lot of network security problems. Today nearly all financial transaction are done through network; social networks are the main mean of communication and there is an effective underlying business on Facebook, Twitter platforms. People exchange sensitive informations via mail, or instant message software as Whatsapp, Telegram. This brings to security holes and it’s important to preserve users by providing security features in applications, such as cryptographic protocols.
Well, advanced cryptography is impossible to break, this make communications safer but there is a counterpart: hackers can use cryptography for evil scopes. A recent threat called **ransomware **that exploit advanced encryption algorithms in order to block system files and demand payment to provide the victim with the key that can decrypt the blocked content. On May 2017 Wannacry ransomware cryptoworm infected more than 230,000 computers in over 150 countries by exploiting a SMB vulnerability [@wannacry] .
Modern approaches to business involve heavy network features, today everything is in the “Cloud”, that brings many economic benefits and creates a link between enterprise and clients, but this add risks due to enterprise exposure. So, an hacker attack can be very expensive for enterprises; according to a McAfee reasearch hackers cost more than $445 Billion annually, due to loss of sensitive data such as credit cards, private business secrets, denial of service attacks [@hackersCost] . Today is the era of Internet Of Things. Small devices such as webcams, dreamboxes, phones are online, maybe with old ftp or telnet services installed by default, with default credentials. These devices are starting point for massive DDoS attacks. This is a very actual risk, and we can see the consequences by looking attacks such Mirai DyN cyberattack on October 21, 2016 that affected most important services in the world such as Amazon, Twitter [@miraiAmazon], Netflix [@miraiNetflix], Wired.
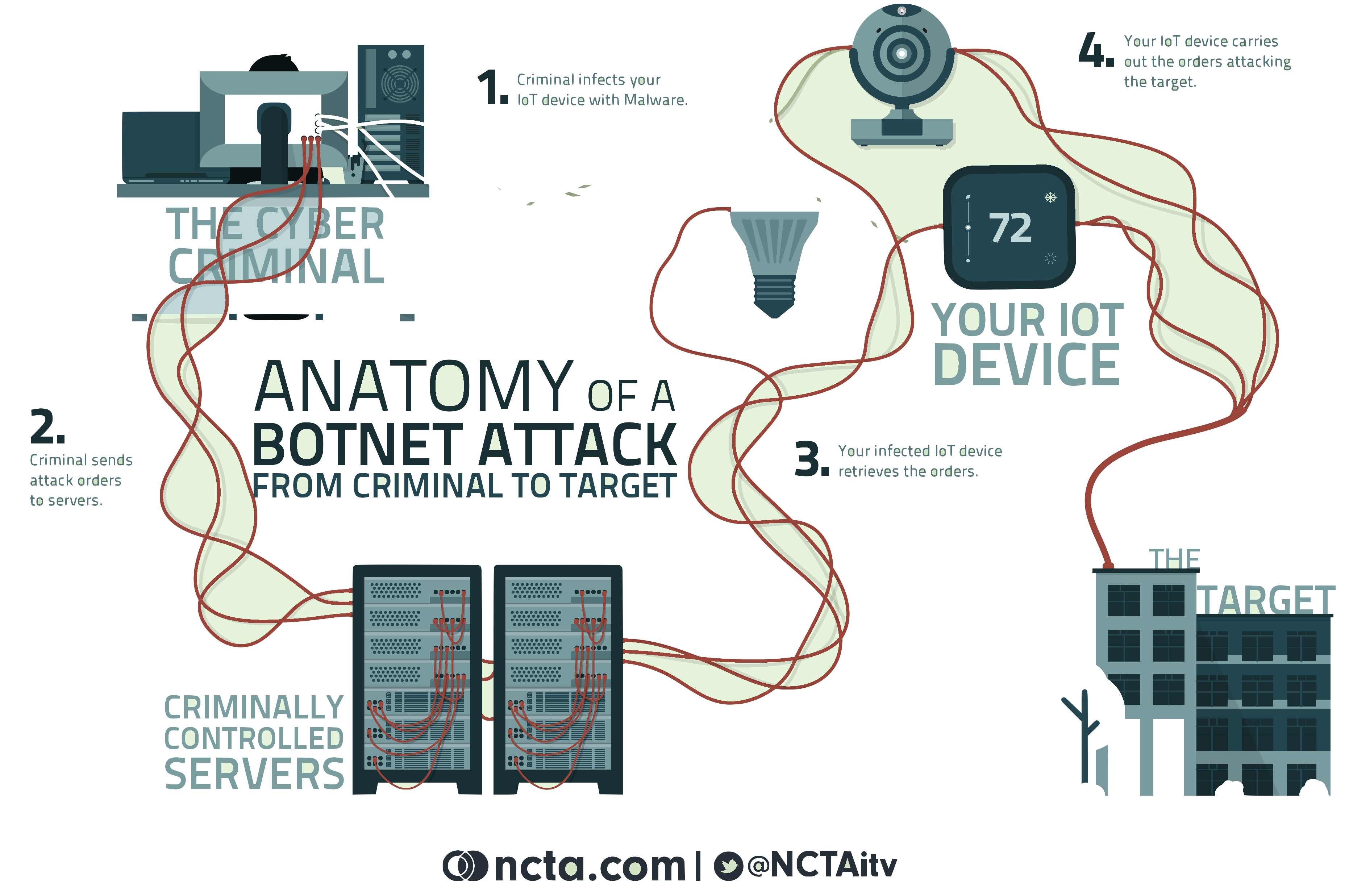
Network security is also a political issue: there are current questions about hacker interferences in elections. Every aspect of this world involves network security. Internet didn’t born for business purposes, so there aren’t native security features in traditional protocols. Today things are completely changed, so it’s important to implement, to understand and to use modern security protocols, such as IPSec, SSL. It’s essential to do security by design, and to think about security in early stages of development process.
Security knowledge is a fundamental aspect for many professional figures: a developer can learn common errors that led to security holes, such as banner grabbing, buffer overflow and off-by-one problems. Testers can learn how to test for security purposes. Administrators can make their networks safer, by securing services and disabling useless services. All these figures need practical examples in order to understand the real problematics of network security. Government laws are severe against hackers. If you are curious and want to experiment a sniffing tool, you could have legal problems: in the worst case you can risk jail:

A famous hacker with legal problems is Kevin Mitnick. He hacked most important companies not for economic purposes but only for his personal “hacking challenges”, and he was sentenced to 46 months in prison [@mitnick]. Now he’s one of the security leader consultant in the world. If you really want to understand network security it’s essential that you understand hacker techniques; security community has created a lot of useful resources that uses virtualization in order to reproduce common vulnerability issues and to avoid legal problems.
State of Art
A lot of programs and tools have been created and released by community with two main scopes: to simplify the penetration testing process and to help beginners in learning network security problems. We can classify these in:
-
Penetration Testing Tools and Distros;
-
Learning Penetration Testing Software;
-
Learning Penetration Testing Environment.
Penetration Testing Tools
Nowadays there is no need to have advanced programming techniques to do a scanning or to exploit a buffer overflow. There are more and more software tools that can help you in every goal you’ve to reach. By following a step by step hacker methodology it’s possible to classify these tools in:
- Footprinting Techniques and Tools Footprinting is the art of gathering informations. An hacker needs to profile target company, by locating ip addresses, domain names, used IDSs, systems’ enumerations, internal domain names, VPNs and related protocols, extranet. It’s an essential phase for security assessment because it gives you a picture of what the hacker sees.
Common techniques involves publicly available informations, such as Google search engine, or web archives (WebArchive) with older web sites version.
Comments in javascript pages of a website can give relevant informations, so tools as **Wget **are used to download all web source code.
Another useful font of information is given by common social networks, such as Twitter, Linkedin. Hackers will search on these sites to find relevant company informations. It’s possible to automate the research process by using tools as ng-recon or **discovery **or Maltego.
By doing a recursive research on Whois Servers hacker can obtain sensitive informations about his target, such as the Registrant, administrative contacts, email, etc. He can also find all ip address associated to a domain.
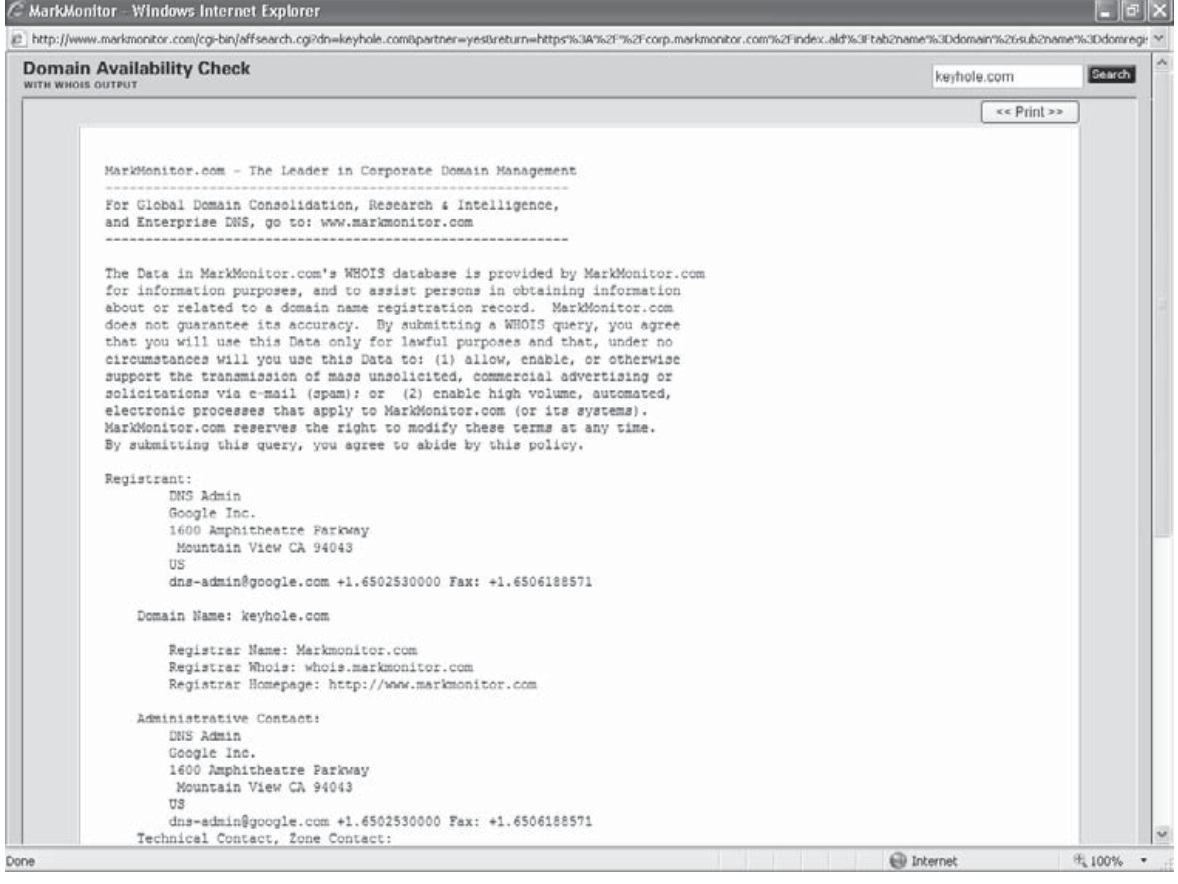
By querying DNS server with techniques as transfer zone and tools as nslookup and dig an hacker can discover many sensitive information about his target, such as which ftp servers are used, internal ip address.
Another step is to determine network topology, and this is done by using traceroute programs, diagnostic programs that lets you view the route that an IP packet follows from one host to the next. With these tools hacker can discover ACLs applied to routers, and network topology.
- Network Scanning Tools To discover vulnerabilities an analysis of open ports in target network is done. The “major” software to do this is nmap [@nmap]. Nmap analyzes each port through different techniques in order to individuate which ports are open and which services are available. It’s possible to do a tcp complete scan port, or a “syn stealth” scanning port that doesn’t complete the three way handshaking (in order to evade IDS detection). Nmap offers a lot of functionalities, such as IP decoy, OS active detection, advanced scripts supports (for example it’s possible to load a script in order to detect if a target is vulnerable to WannaCry). So, Nmap is not only a simple network scan, but it’s a complete network analysis tool.

Another network scanner tool to mention is masscan [@masscan]. Masscan doesn’t offer all Nmap functions but it’s very fast. A common approach is to do a massive scan with this tool in order to find all open ports in a large network, then use Nmap to do an advanced network scan analysis.
- Vulnerability Assessment tools: a great support to penetration testing is given by automated tools that analyze a network to discover all available services and their vulnerabilities. Common used tools are NeXpose [@nexpose], Nessus [@nessus], OpenVas [@openvas] .
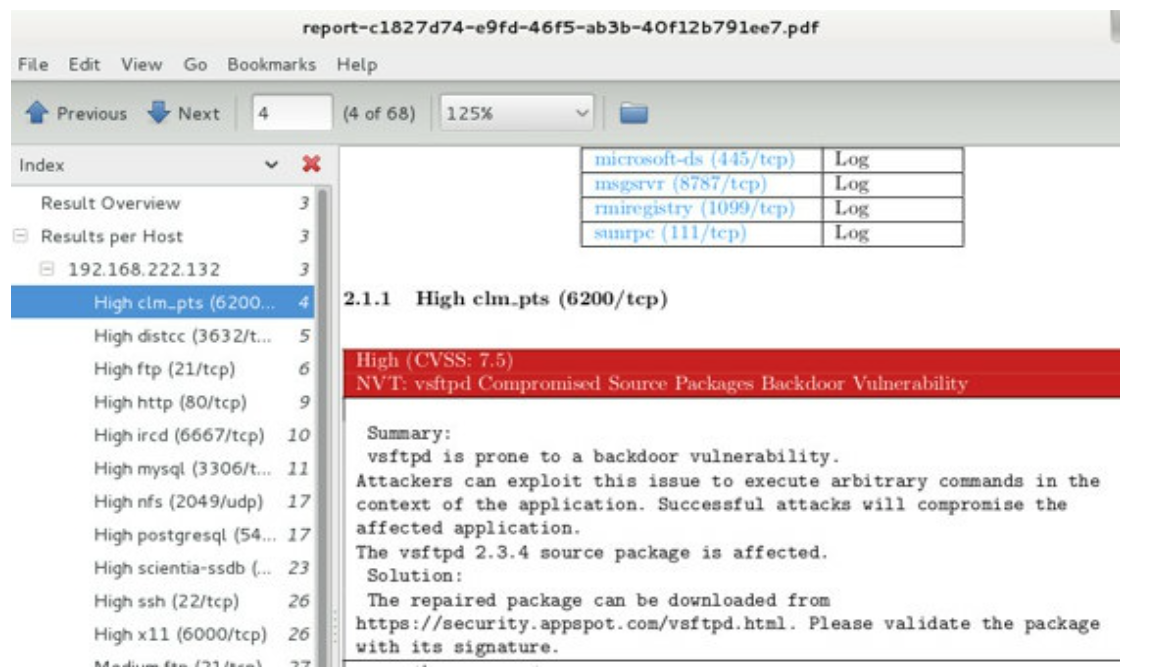
About web vulnerabilities specific scanners have been developed: a common one is Nikto [@nikto], a generic web scanner that reveals a lot of common web server problems, such as information disclosure, misconfiguration problems, vulnerable installed software, etc. There are also CMS specific vulnerability scanners, such as WPScan [@wpscan] for Wordpress, JoomlaAttack for Joomla.
-
Exploit and Post-Exploit Tools A complete framework to exploit vulnerabilities exists: **Metasploit **[@metasploit]. Metasploit is the most used penetration testing software, it contains a rich exploit database that allows you to simulate real-world attacks on your network to train your security team about security issues. Metasploit framework also includes other tools such as nmap, NeXpose and it can do a complete vulnerability assessment by only using this tool. It provides advanced post-exploit elements such as Meterpreter that enables users to control the screen of a device by using VNC and to browse, upload and download files. Metasploit is an open source project, and exploits are written in Ruby language, so it is fully configurable.
-
Network sniffing Another used technique by hackers is to sniff network with the aim of detect sensitive informations such cleartext passwords. There are many tools to do this, two commons are **tcpdump **[@tcpdump] and **Wireshark **[@wireshark]. TCPDUMP has a simple command line interface, while Wireshark offers a complete GUI interface with wonderful features such as an advanced filtering syntax, follow tcp stream option, etc.

All these tools uses a standard format for save data (pcap format), so it’s possible to combine them, for example to sniff with tcpdump on a compromise network, to save data in pcap format and to analyze data offline with Wireshark.
-
Password strength It’s important to test the strength of password rules in a company. To do this a bruteforce or dictionary attack is sent to all authentication login pages. Authentication login is present on ftp, telnet, ssh servers, such as login http basic authentication or post forms on a website. Default credentials will be submitted, information disclosure about usernames or password rules will be analyzed, then the attack will be sent through tools as hydra [@hydra], or some web proxy as ZAP. An hacker also tests for decrypting hashed password by using tools as John The Ripper [@john].
-
Web applications security tools There are specific tools to do a semiautomatic analysis of web vulnerabilities. These tools intregrates a lot of features, such as web proxy, customization of GET and POST requests, request repeaters, web spidering, fuzzing data sender. A very used commercial tool is Burp Suite [@burp] of PortSwigger. An amazing open source tool is Zed Attack Proxy (from OWASP project) [@zap]
-
Penetration testing distros Advanced Penetration Testing Linux Distribution have been developed. Most famous is **Kali **(successor of Backtrack) [@kali], a Debian GNU/Linux distribution created by Offensive Security that contains a large collection of security and forensic tools, such as Wireshark, John the Ripper, aircrack-ng. There is also an arm version that can run on Raspberry-Py.
Learning Penetration Testing Software
A lot of vulnerable software is available online. On vulnhub site [@vulnhub] there is an unlimited list of vulnerable VMs and vulnerable software to run in order to practice. Every day a new challenge is loaded on site.
Metasploitable and DamnVulnerableLinux [@damn] are very vulnerable Linux distros that can be used to test commons services exploits, and privilege escalation. These VMs are commonly used to learn the basics of Metasploit
All vulnerability online databases are an excellent resource to learn common vulnerabilities. exploit-db [@exploitdb] for example gives a vulnerability description, provides source code to exploit the vulnerability and sometimes also gives source code of application vulnerable app, so you can compile it on a virtual machine and try to exploit the vulnerable service.
About Web Application vulnerabilities, OWASP project [@owasp] is an online community which creates freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security. OWASP offers a lot of training materiale and a completely vulnerable website with target, called WebGoat that can be used to understand most common web vulnerabilities, such as SQLi, XSS, CSRF. Other important website distros are bodgeit, DamnVulnerableWebApps
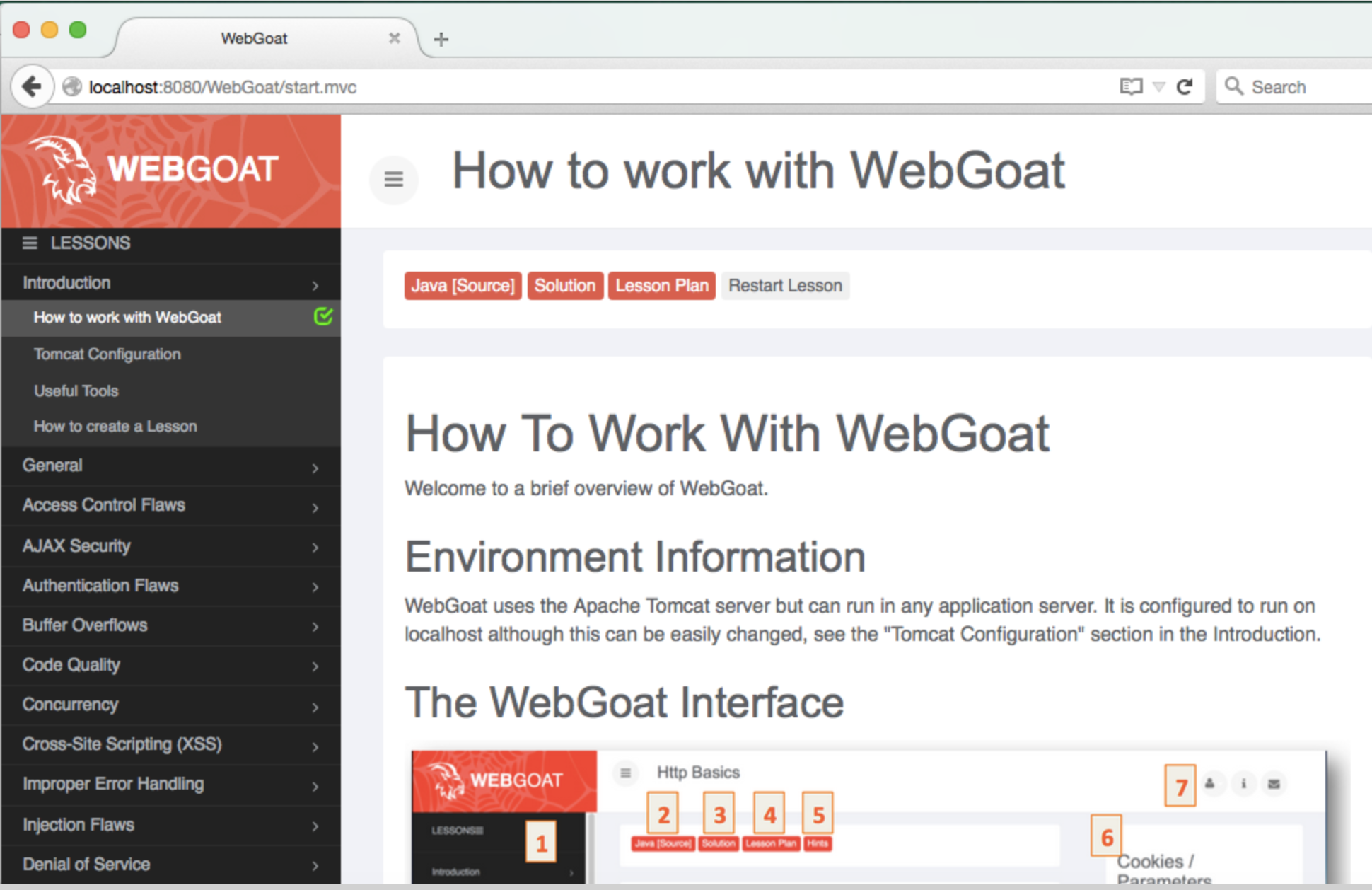
Learning Penetration Testing Virtual Environment
A lot of security resources have been developed to learn network security features. Offsensive Security offers commercial professional course training by providing virtual penetration testing labs and by offering different types of Security Certifications:

Metasploit is used to exploit all basics labs vulnerabilities. Metasploit could require some little modification to work with different environments, so for a penetration tester it’s important to learn about buffer overflow basics. A good online environment is Over the wire (http://overthewire.org/wargames/narnia/), that provides different CTF challenges where you’ve ssh access and you’ve to exploit some vulnerable services to win the challenge.

A modern approach to network security: Docker
With the growing tendency of container-based virtualization, many developers are working to convert network security tools and virtual environments are in Docker images.
Docker provides a microservice architecture, so each tool can be converted in a specific Docker image (for example nmap can be implemented as a Docker nmap image). Docker images also gives full support to vulnerable services: currently WebGoat, DVWA, bodgeit and many other applications are implemented in Docker images. On DockerHub registry there is a growing tendency to implement Docker vulnerable images, because of the flexibility that this technology gives to users. Docker Security Playground uses all these created images and offers a platform to use them.
There is almost nothing about the use of Docker-Compose as a complete security labs’ platform, even if on the web it’s possible to see that there are preliminary uses of Vagrant to simulate vulnerable network environment.
The innovation of Docker Security Playground is to use Docker-Compose to generate vulnerable IaC labs, by offering a flexible and lightweight platform to create, manage and simulate virtual vulnerable environments by using docker images, without the cost of a complete virtualization such as VBox or VmWare. Docker Security Playground also provides a docker images standard (Docker Image Wrapper) to automate the virtual labs’ development. Actually many images have been developed, such as:
-
a full kali image distro with shellinabox support (that can be used to navigate the OS via browser), metasploit, and all most important network security tools discussed previously With Docker Security Playground is possible to implement a real enterprise scenario such as Offensive scenarios and to simulate hacker attacks, in order to practice about network security aspects;
-
a router base image with iptables support to simulate firewalling scenarios;
-
a lamp web server to simulate php vulnerable web services
What Now?
Go to Virtualization