-
-
Notifications
You must be signed in to change notification settings - Fork 384
FS_BitLocker
The directory misc/bitlocker exists as a sub-directory to the file system root.
The directory contains identified bitlocker encryption keys in formats which allows for easy unlocking of the bitlocker volumes.
The files in the misc/bitlocker directory are listed in the table below:
| File | Description |
|---|---|
| readme.txt | General information about the bitlocker module. |
| .bin | The binary in-memory representation of a key. |
| .fvek | Dislocker unlock key (see below). |
| .txt | Text representation of a key. |
Files in the misc/bitlocker directory is read-only.
The bitlocker plugin is loosely based on the excellent bitlocker volatility plugin. The MemProcFS plugin uses the same underlying technique of identifying potential bitlocker keys by pool tagging and other heuristics. The MemProcFS plugin also does some post-processing to increase output quality.
The bitlocker plugin works quite well on Windows 7 and Windows 10/11. Issues however exists on Windows 8 (and early Windows 10) versions where multiple keys may be recovered in error. At least one key should however most often be correct even on Windows 8 and early Windows 10 versions.
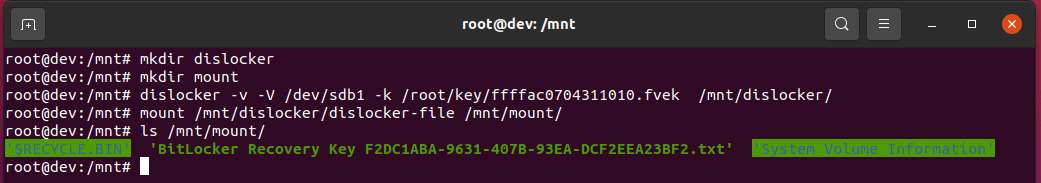
In order to mount a recovered bitlocker key it's recommended to use dislocker on a Linux system. Please use the recovered .fvek key.
dislocker -k <recovered_key>.fvek /path/to/disk /path/to/dislocker
mount /path/to/dislocker/dislocker-file /path/to/mount
Please see an example of the mount process using dislocker in the example section below.
The example shows the misc/bitlocker directory with a recovered bitlocker key.
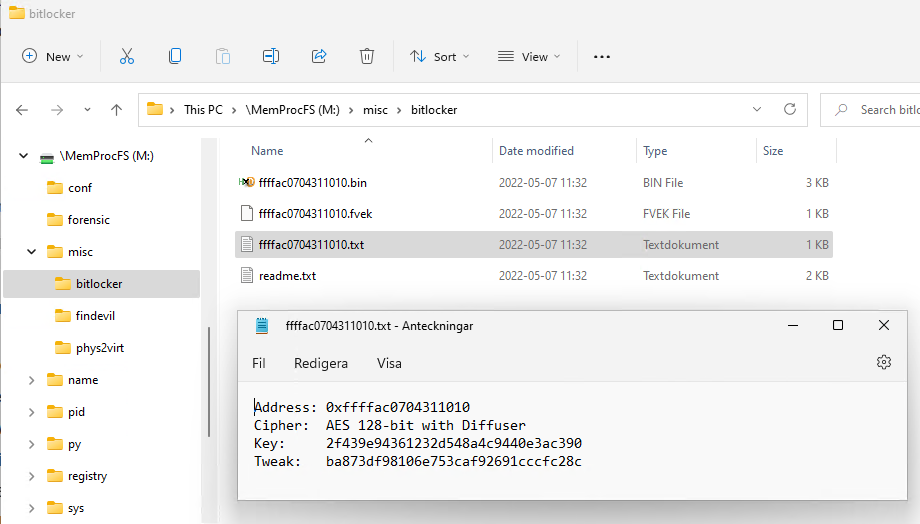
The image below shows how its possible to mount a bitlocker encrypted drive by using dislocker and the recovered .fvek key.
The misc/bitlocker sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file modules/m_misc_bitlocker.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖