-
-
Notifications
You must be signed in to change notification settings - Fork 384
FS_Forensic_Files
The directory forensic/files exists as a sub-directory to the file system root.
The directory is hidden by default. It will appear once forensic mode has been started and processing is completed.
The directory contains a best-effort reconstructed file system reconstructed from potentially recoverable file objects in the kernel. The file objects are retrieved from the kernel pool and process handles.
The file files.txt contains a complete record of the recovered files and their path. It's also possible to view the recovered files by clicking around in the sub-folders. Please note that the reconstruction is a best-effort reconstruction and may contain errors as well as missing files and folders.
Also see the NTFS MFT file recovery module - which may recover small files not visible in this module.
| File | Description |
|---|---|
| readme.txt | README file. |
| files.txt | Files recovered |
The file files.txt have the following format:
# OBJECT_ADDRESS TYPE SIZE NAME PATH
=================================================================
0000 ffff8e03a085a830 D--- 2560 svchost.exe.mui \Windows\System32\en-US\svchost.exe.mui
0001 ffff8e03a0a96670 D--- 17920 oleaccrc.dll.mui \Windows\System32\en-US\oleaccrc.dll.mui
0002 ffff8e03a0a9a1d0 D--- 5632 twinui.pcshell.dll.mui \Windows\System32\en-US\twinui.pcshell.dll.mui
...
01b0 ffff8e03a7809950 DC-- 1118208 System.evtx \Windows\System32\winevt\Logs\System.evtx
01b1 ffff8e03a780a120 DC-- 5312512 Security.evtx \Windows\System32\winevt\Logs\Security.evtx
01b2 ffff8e03a780a2b0 DC-- 1118208 Windows PowerShell.evtx \Windows\System32\winevt\Logs\Windows PowerShell.evtx
...
| TYPE | Description |
|---|---|
D |
Data backed file |
C |
Cache backed file |
I |
Image backed file |
X |
Duplicate file (file exists with same name and contents, but different file handle) |
Files in the forensic/files directory and its sub-directories are read-only.
The example shows browsing of the recovered file system, as well as listings of the files in the file files.txt.
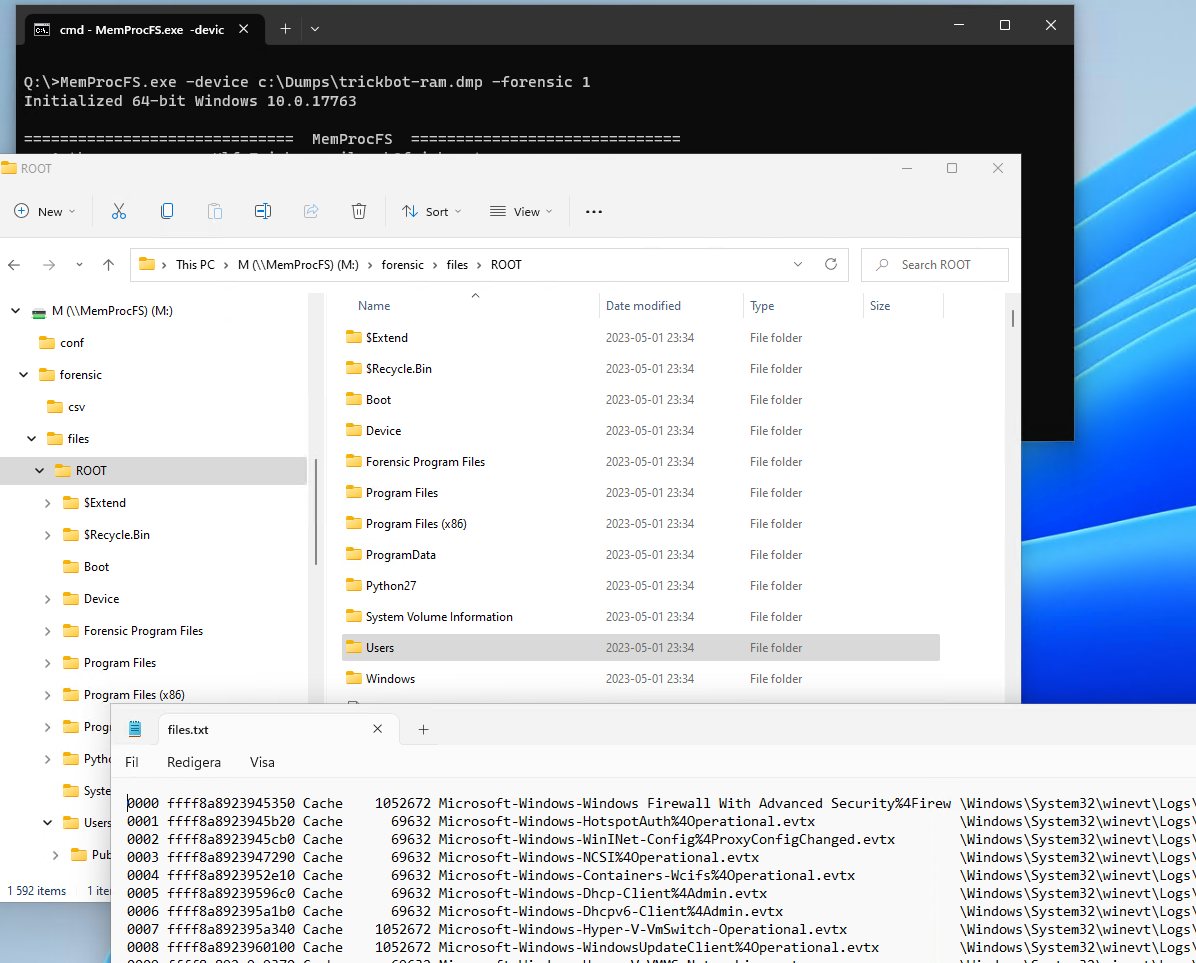
The forensic/files sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file modules/m_fc_file.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖