-
-
Notifications
You must be signed in to change notification settings - Fork 384
FS_Process_Heaps
The directory heaps exists as a sub-directory in each process directory.
The heaps directory contains one sub-directory for each heap as well as info files about the heaps.
Each module directory contains a number of informational files and directories related to the loaded module. The files and directories and their contents are listed below:
| File | Description |
|---|---|
| readme.txt | Readme with information about the heap parsing. |
| heaps.txt | Information about the process heaps. |
| segments.txt | Information about the segments (memory ranges) related to the heaps. |
| [heap-id]/allocations.txt | Heap allocations for the specified heap. |
| [heap-id]/allocations-v.txt | Heap allocations and the first 16 bytes for each allocation. |
| [heap-id]/[num]/[addr].mem | Heap allocation memory |
The heap module parses NT heaps as well as segment heaps (on Windows 10 1809/17763 and later).
Text files are read only. .mem files in sub-directories are writable if a write-capable memory acquisition device is used.
The file heaps.txt contains information about heaps related to the process. The meaning of the different columns are as follows:
# PID Heap Address Type
--------------------------------------
0000 3668 1 0000000000c90000 Nt
0001 3668 0 00000000011e0000 Nt
0002 3668 2 0000000001380000 Nt
0003 3668 3 0000000002cb0000 Nt
0004 3668 60 00000000032e0000 Nt
The file segments.txt contains information about the heap segments (memory ranges). The meaning of the different columns are as follows:
# PID Heap Address Type
--------------------------------------
0000 3668 1 0000000000c90000 NtSegment
0001 3668 0 0000000000dd0000 NtLfh
0002 3668 2 0000000001170000 NtLfh
0003 3668 0 00000000011e0000 NtSegment
0004 3668 2 0000000001380000 NtSegment
0005 3668 3 0000000002cb0000 NtSegment
0006 3668 59 0000000003000000 NtLfh
0007 3668 60 00000000032e0000 NtSegment
The file allocations-v.txt contains information about heap allocations related to a specific heap. HexAscii16 in the -v file contains the first 16 bytes of each heap allocation. The meaning of the different columns are as follows:
# PID Heap Address Size Type HexAscii16
--------------------------------------------------------------
0000 3668 0 00000000011e0750 2c Nt 43 00 3a 00 5c 00 57 00 69 00 6e 00 64 00 6f 00 C.:.\.W.i.n.d.o.
0001 3668 0 00000000011e07a0 52 Nt 43 00 3a 00 5c 00 57 00 69 00 6e 00 64 00 6f 00 C.:.\.W.i.n.d.o.
0002 3668 0 00000000011e0810 38 Nt 80 74 1e 01 00 00 00 00 88 33 9f e2 fa 7f 00 00 .t.......3... ..
0003 3668 0 00000000011e0860 f0 Nt 10 20 20 01 00 00 00 00 f0 84 1e 01 00 00 00 00 . .............
0004 3668 0 00000000011e0970 1c8 Nt 02 00 00 00 00 00 00 00 c0 b1 9a e2 fa 7f 00 00 ............. ..
0005 3668 0 00000000011e0b50 1c8 Nt c4 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0006 3668 0 00000000011e0d30 38 Nt 30 0d 1e 01 00 00 00 00 30 0d 1e 01 00 00 00 00 0.......0.......
0007 3668 0 00000000011e0dc0 f0 Nt 80 16 20 01 00 00 00 00 60 31 6f 04 00 00 00 00 .. .....`1o.....
The example below shows the files in the heaps/0 sub-directory of the cmd.exe process where 0 is the heap id. It shows an overview of verbose allocations in heap 0 as well as an overview of the process heaps.
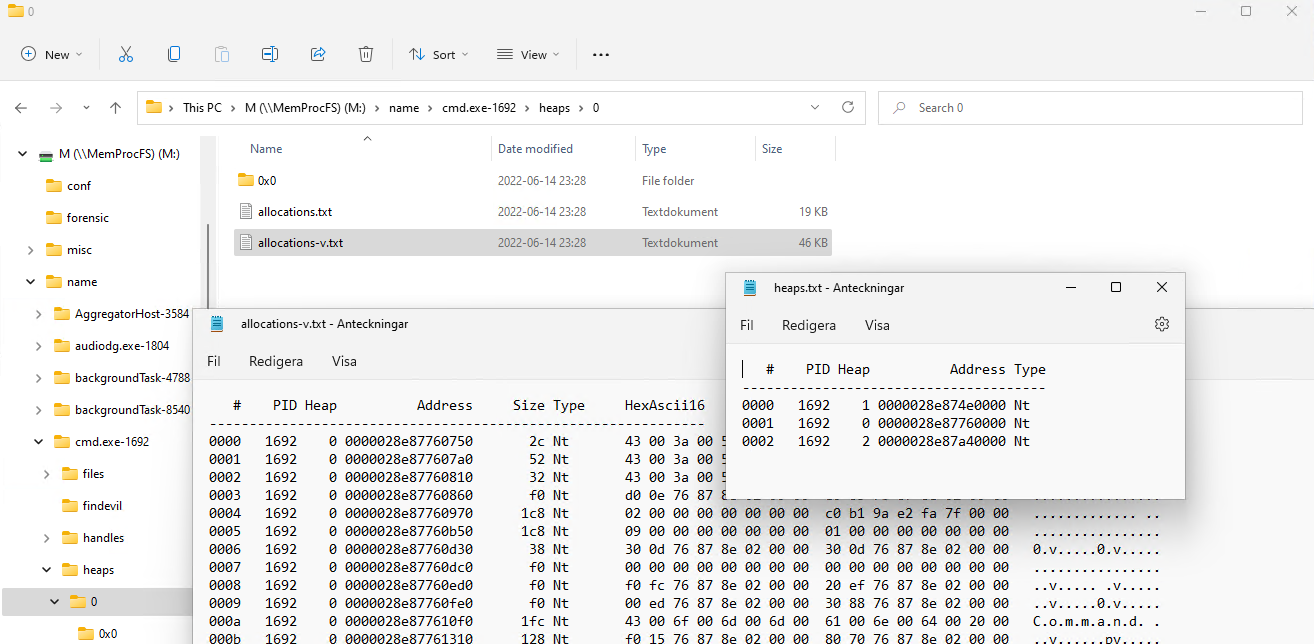
The heaps sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file modules/m_proc_heap.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖