-
Notifications
You must be signed in to change notification settings - Fork 388
LDAP Authentication
- Overview
- Configuration steps for Enterprise, AWS, and Team Editions
- Configuration steps for CloudBeaver Community Edition
LDAP (Lightweight Directory Access Protocol) is a protocol designed to manage and access distributed directory information services over an Internet Protocol network. LDAP is used to store and retrieve data in a hierarchical directory structure, such as usernames and passwords, organizational units, and configuration settings. It facilitates directory management and authentication processes, allowing for a centralized approach to maintaining user credentials and policy settings.
For comprehensive guidance on configuring and managing LDAP, refer to the official LDAP documentation.
-
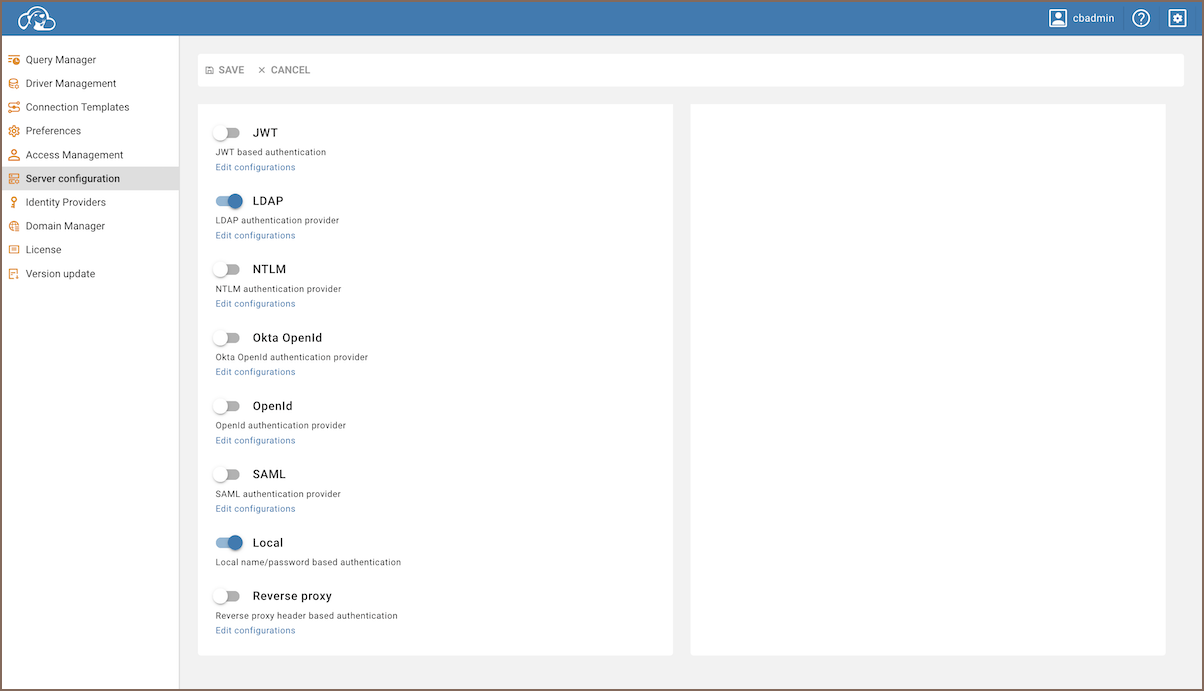
As an administrator, go to Settings -> Server Configuration.
-
Find and activate the LDAP option in the Configuration section.
-
Save the changes.
-
As an administrator, navigate to Settings -> Identity Providers.
-
Click on the + Add button.
-
Fill in the following fields:
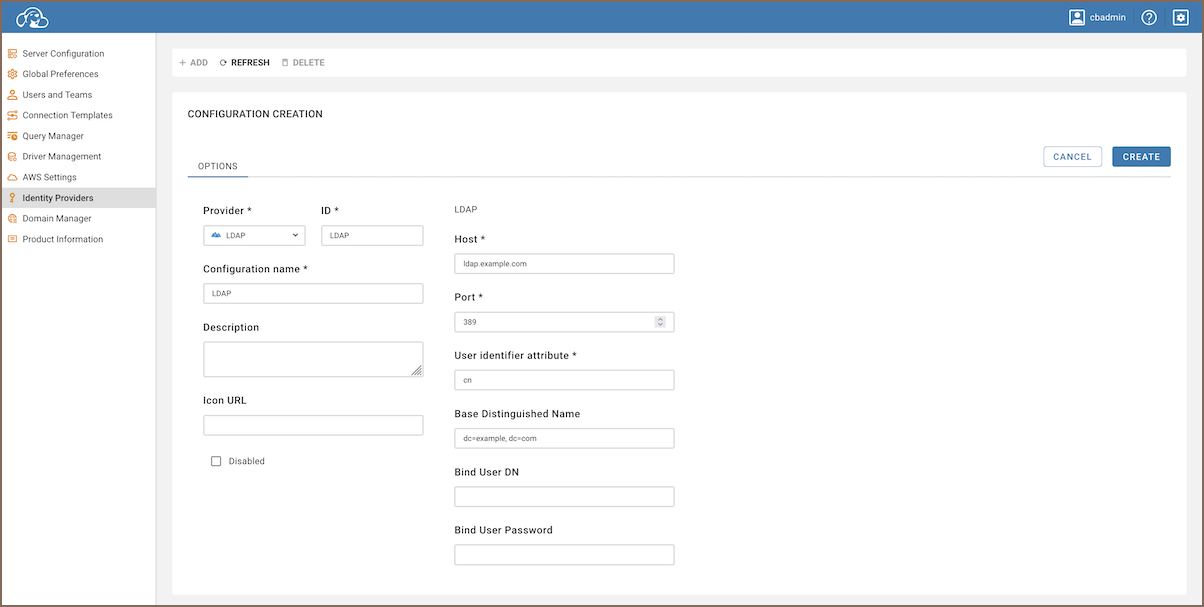
Field Description Parameters used to configure LDAP in the CloudBeaver Community Provider Select LDAPfrom the dropdown menu.ID Enter a unique identifier for the configuration. Configuration name Enter a descriptive name for this configuration. Description (Optional) Provide a brief description of this identity provider configuration. Icon URL (Optional) Enter the URL of an icon to represent this provider. Disabled (Optional) Leave unchecked to enable this identity provider. Host Enter the server hostname or IP address where LDAP authentication is handled. ldap-host: ""Port Specify the port number used for LDAP communication. ldap-port: ""User identifier attribute Enter the attribute used to uniquely identify LDAP users. Default value in PRO versions is cn.ldap-identifier-attr: ""Base Distinguished Name (Optional) Enter the Base Distinguished Name (DN) for LDAP queries. It should be in the format appropriate for your LDAP directory, such as dc=example,dc=com. If not explicitly specified, this value will be automatically appended to the end of the User DN during authorization.ldap-dn: ""Bind User DN (Optional) Enter the Distinguished Name (DN) of the user who has permissions to search for entries (e.g., users) in the directory. This user will be used to verify access to the application with the specified filter. ldap-bind-user: ""Bind User Password (Optional) Enter the password associated with the Bind User DN account. ldap-bind-user-pwd: ""User Filter (Optional) Specify criteria for searching specific entries (users, groups, attributes). The filter must always be written in parentheses. Logical operators are supported. ldap-filter: "()"Tip: You can specify organizational units within the Base Distinguished Name to streamline access, such as
ou=unit1,dc=example,dc=com. These can be set during the Identity Provider setup or during login in CloudBeaver. -
Click on the Create button.
-
With the LDAP configuration now established, proceed to the login screen.
-
Select the LDAP authentication method.

-
In the User DN field, enter the Distinguished Name (DN) of the user who is logging in. This specifies the exact entry within the LDAP directory associated with your user account.
-
Enter your User password in the corresponding field to authenticate.
Note: If the Base Distinguished Name was specified during the setup of your LDAP configuration, it will be automatically appended to the User DN if not explicitly included. This can simplify the login process, especially when managing multiple users.
-
After entering the required information, click Login to access the application.
In CloudBeaver Community Edition, configuration settings are not accessible through the user interface (UI). Instead, settings must be configured directly within the workspace configuration file.
Steps to configure LDAP in Community Edition:
- As an administrator, go to Settings -> Server Configuration and activate the LDAP option in the Configuration section.
- Locate either the
.cloudbeaver.runtime.conffile to configure LDAP for the current workspace or the.cloudbeaver.conffile to set the LDAP provider for all newly created workspaces. More details can be found in the server configuration guide. - Open the file with a text editor to modify or add LDAP configurations.
- Insert the following configuration snippet into your configuration file under the
app.authConfigurationssection. Adjust the parameters according to your LDAP server details.
"authConfigurations": [
{
"id": "ldap",
"provider": "ldap",
"displayName": "LDAP",
"disabled": false,
"iconURL": "",
"description": "",
"parameters": {
"ldap-host": "ldap.example.com",
"ldap-port": "1389",
"ldap-dn": "ou=users,dc=company,dc=com",
"ldap-identifier-attr": "cn",
"ldap-bind-user": "cn=serviceAccount1,ou=serviceAccounts,dc=company,dc=com",
"ldap-bind-user-pwd": "serviceAccount1password",
"ldap-filter": "(givenName=*)"
}
}
]Important: Ensure that the
provideris set toldap.
-
After editing the configuration file, restart CloudBeaver for the changes to take effect.
- Application overview
- Demo Server
- Administration
- Supported databases
- Accessibility
- Keyboard shortcuts
- Features
- Server configuration
- CloudBeaver and Nginx
-
Domain manager

- Configuring HTTPS for Jetty server
- Product configuration parameters
- Command line parameters
- Local Preferences
-
Team Edition Overview

-
Getting started with Team Edition

-
Team Edition Server Configuration

-
Projects in Team Edition

-
Teams in Team Edition

- Team Edition Deployment
-
Roles in Team Edition

-
Git integration in Team Edition

-
Datasets in Team Edition

-
CloudBeaver Community
-
CloudBeaver AWS
-
CloudBeaver Enterprise
-
Deployment options
-
Development